Your Privacy:
Privacy Policies, End User License Agreements (EULAs), and Terms of Service (TOS) are important things to look for whenever you visit a web site or install new software. I'm a believer in clear, succinct, straightforward Privacy Policies.
To that end, you should know that I do not and will never...
- use JavaScript or any other type of "active content" to track or monitor your online behavior;
- use banner ads or popups to "defray" the (minimal) costs of maintaining this web site;
- partner with any third party company or organization for any purpose or exchange any data
about usage of this web site with a third party.
The webserver for SpywareWarrior.com does record and compile
statistics on "page hits." Moreover, the webserver software reccords your IP
address, what web page you came from to visit the site, and what pages you visit
while at the site. None of this data identifies you personally, however, and I
do not view any of this data myself (though the webmaster for SpywareWarrior.com
does so on a periodic basis). More importantly, none of the data gathered by the
webserver is shared with third parties under any circumstances.
If you contact me via email with questions or issues regarding either this site or the information you find on it, I may need to get advice from a third party (e.g., on a newsgroup) in order to address your questions and concerns. In such cases I will not disclose any identifying information about you (though I may quote or summarize parts of your email).
If do you experience or detect any unseemly activity that you can verifiably attribute to your visit to this web site, I would be most interested in hearing about it. You can email me at:
You can get my PGP public keys HERE.
What follows on the remainder of this long-ish web page is a
discussion of Privacy Policies, privacy "seals," and other public relations gimmicks that many corporate web sites use to stifle discussion about and action on the very real privacy problems that ordinary Internet users face.
The Problem
w/ Privacy Policies
& "Industry Self-Regulation"
|
The
Problem with Privacy Policies & "Industry Self-Regulation"
That Having Been Said...
I must tell you that the use of Privacy Policies can only go so far in protecting your privacy online. I am equally skeptical of the "seal" programs that have been erected around the use of Privacy Policies (e.g., TRUSTe, BBBOnline , NetTrust, or CPAWebTrust). And despite the hype from Microsoft and others, the P3P program, as well as its implementation in Internet Explorer 6.0, isn't much better. Privacy Polices and "seal" programs are not, as some would have you believe, the be-all-and-end-all of online privacy. Nor can the use of Privacy Policies and "seals" by private companies and organizations serve as evidence that the "free market" is capable of protecting the privacy of "netizens" independent of sound national legislation.
Privacy Policies and "seal" programs are at the heart of the case that opponents of privacy legislation make for industry "self-regulation." There are several fundamental problems, however, with the faith laid in privacy policies and the privacy seal programs that sometimes govern
them.
A Fundamental Conflict of Interest
First, one serious flaw in these privacy seal programs (and other similar attempts at "self-regulation") is the very basic conflict of interest which lies at the heart of such arrangements: privacy seal programs like TRUSTe, BBBOnline, or CPAWebTrust are financially dependent on money received from the very web sites and companies they are supposed to be policing. That's a fundamental conflict of interest built on dirty money, and all the professed good intentions found in the endless flood of breathless, over-hyped press releases that emanate from the parties involved cannot wash clean the flawed financial relationship between the seal programs and the sites they are charged with overseeing. These programs have been
compromised from the start.
Opt-Out, Not Opt-In
Second, these seal programs allow companies and web sites to base their privacy polices on the principle of "opt-out." An "opt-out" privacy policy means that a web site or company can collect and share personal information about you unless and until you tell them to stop. In other words, the site or company is free to exploit your privacy for whatever purposes it chooses unless you contact them to put an end to it by "opting out."
As you can well recognize, "opt-out" privacy policies depend on consumers' recognizing that there might be a problem, seeking out and wading through the
complex legal minutiae of such privacy policies, and then figuring out how to go about "opting out." That few would ever succeed in doing so is to be expected. Still further, should you finally succeed in "opting out," you may not have accomplished as much as you think you have:
- Many of these "opt-out"" plans are time-limited, meaning that you will get a reprieve from a company's privacy invasive practices for only a short duration (a month, for example). After the designated period of time passes, you will again be subjected to those invasive practices until you "opt-out" again. In effect, these time limits force you to engage in an on-going relationship with a company or web site that you would rather have nothing to do with.
- If your privacy preferences become too inconvenient for the company or web site, they just may decide to revise their privacy policies or "reset" your recorded privacy preferences, insisting that there must have been a mistake. AOL and eBay have done just this to their customers and clients in the past few years or so. (1, 2, 3, 4) Yahoo! performed this same switcheroo on its customers in March of 2002. (1, 2, 3) Microsoft quickly followed suit in May of 2002, resetting the privacy preferences of Hotmail users. (1, 2, 3, 4) Not wanting to be left out of the game, Best Buy ripped the rug out from under its customers in June of 2002. (1) Walt Disney Corporation decided that it's privacy policy wasn't invasive enough, so it revised it, giving itself the right to collect and link all manner of personal information from you and your children. Amazon, of course, was an industry leader in this regard, breaking its privacy promises to customers two years ago when it revised its privacy policy (1, 2). Amazon recently announced that planned to revise its policy yet again (1, 2). Clearly, these companies either do not understand or simply refuse to heed the word "No."
- Companies that do allow you to "opt-out" will still throw plenty of barriers in your way to discourage you from doing so. Still worse, some companies will regard your attempt to "opt-out" as merely another opportunity to badger you to accept their poor privacy practices. Not satisfied with having violated its own privacy policy and handed over information on millions of customers to the Defense Department in the Jet Blue fiasco, Acxiom has decided that to serve you better it will refuse to honor "opt-out" requests unless you give the company a chance to talk you out of it.
- Some companies will even punish
you, should you dare to opt-out of their exploitative information
practices.
- You have almost no means even to verify that your personal information is not being shared with other entities after you have submitted your "opt-out" request.
- Some of the EULAs and Privacy Policies used by companies include clauses that actually require you to
waive your right to hold those companies responsible for the security of your sensitive, private information. In other words, you are
required to "opt out" of your own rights as a consumer.
- Don't be fooled! Some companies have started to resort to clever wording in their privacy policies to give the impression of an "opt-in" policy. For example,
this privacy policy states that, "We do not sell or rent your personally identifiable information to third parties for marketing purposes without providing you with a choice to opt out from such disclosure..." Notice how the wording initially appears to provide strong protections for your personal information, when in fact this policy is really only the standard opt-out policy used by most companies -- they can do anything they want with your personal information unless you explicitly tell them not to.
By contrast, this
privacy is much more strongly worded and is, in fact, a true opt-in policy:
"Unless we tell you otherwise, we do not sell or rent your personally-identifiable information to any third parties unless we have received your approval to do so."
"Opt-out" privacy policies are not designed to protect your privacy; they're designed to allow companies and web sites to continue their invasive practices while giving them a convenient alibi. In short, an "opt-out" privacy policy is next to worthless. eBay, for example, even brags
about the "flexibility" of its "privacy policy" and how that "flexibility"
essentially allows them to do what they will. By contrast an "opt-in" policy prohibits such behavior until you explicitly give a company or web site permission to collect and share personal information.
Bankruptcy & Acquisition Change All the Rules
Third, any privacy protections that might be extended in these privacy policies go out the window should the companies go bankrupt or be acquired by other companies. As has been demonstrated in several cases so far, companies facing financial ruin or corporate merger can and do renege on the promises made in privacy policies because the data they have collected represent valuable assets. Many companies actually provide for these eventualities right in their privacy policies. When the financial going gets rough, your privacy will take a back seat to the needs of creditors and investors, and there is very little these privacy seal programs (or you, for that matter) can do about it.
IE6 & P3P Are Not Panaceas
Fourth, the implementation of P3P (Platform for Privacy Preferences) in Internet Explorer 6.0 does not provide significant privacy protections that are actually usable by the majority of people who browse the web with Internet Explorer. Users who are concerned about their privacy online would be much better off abandoning the default P3P-based Privacy Settings slider bar and pursuing other alternatives for handling cookies in Internet Explorer 6.0.
- The default Privacy settings for Internet Explorer 6.0 are lax and provide no meaningful privacy protection. At the default "Medium" setting, most cookies are accepted, even those from major third-party advertisers and marketers like Doubleclick (see THIS page and THIS page for details). Thus, IE 6.0 puts the onus on users (not the web sites) to put a stop to privacy invasive practices of web sites. And to take back their privacy, those users -- who might have initially thought IE 6.0 would significantly improve their privacy protection straight "out-of-the-box," given all the hype -- will have to figure out IE 6.0's complicated Privacy settings themselves. And just how clear and helpful are those Privacy settings? Not very.
- The Privacy Settings slider bar is only marginally helpful. Most users who look into configuring IE 6.0's Privacy settings will resort to the Privacy Settings slider bar, but this slider bar gives only the illusion of simplicity and safety. While descriptions for main slider settings are provided, most users will fail to understand that underneath these settings lies a complex interpretation of P3P compact policies posted by web sites. And the way that IE 6.0 interprets and reacts to these P3P compact policies across the various slider setting levels is incredibly complex and inconsistent.
All of this is, of course, hidden from users behind simplistic terms, and no normal user could reliably predict what cookies will be accepted or blocked at the various slider levels, except for the very highest and lowest levels. Lest you doubt, what follows is a table detailing the ways that different types of cookies are handled by IE 6.0 at the various slider settings based on web sites' compact policies:
The Privacy Settings Slider Bar
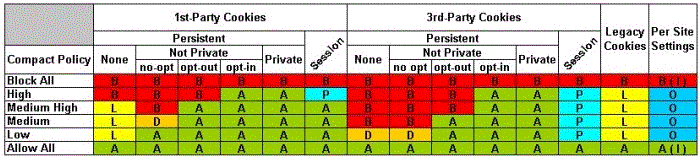
(Click for full size image)
Cookie Types:
| 1st-Party: |
the site (URL) you are visiting |
| 3rd-Party: |
NOT the 1st-party site you are visiting (not the "top-level" URL), but another site which places content on that 1st-party site |
|
-- Persistent: |
permanent cookies that are saved for future use to your hard drive |
|
-- Session: |
temporary cookies that are deleted from memory when the browser is closed |
| Legacy Cookies: |
cookies present before IE 6.0 was installed |
| Per Site Settings: |
web sites specifically entered in the Privacy tab's "Per Site Privacy Actions" box |
Compact Policy:
| None: |
No Compact Policy exists on the web site |
| Not Private: |
"Personally identifiable information" IS used by the web site |
| -- no opt: |
The site gives you no choice over its use of "personally identifiable information" (no "consent") |
| -- opt-out |
The site can use "personally identifiable information" until you tell them to stop ("implicit consent") |
| -- opt-in: |
Before the site can use "personally identifiable information," you must give your permission ("explicit consent") |
| Private: |
NO "personally identifiable information" is used by the web site |
Note: a Compact Policy is computer readable P3P policy that a web site transmits specifying how it will use your personal information. IE 6.0 distinguishes between "acceptable" and "unacceptable" ("satisfactory" and "unsatisfactory") compact policies and cookies:
- An "unacceptable" compact policy is one that provides for the use of "personally identifiable information," but without users' "consent" (via an opt-in or opt-out policy).
- An "acceptable" compact policy either specifies no use of "personally identifiable" information at all, or provides for the use of "personally identifiable information," but with users' consent (via an opt-in or opt-out policy).
Results:
 |
B |
= |
Blocked |
Cookies are "denied" |
 |
A |
= |
"Accepted" |
Cookies are "allowed" |
 |
L |
= |
"Leashed" |
Cookies are limited to use in 1st-party contexts only |
 |
D |
= |
"Downgraded" |
Cookies are "restricted" to the current browser session (turning them into Session cookies) and deleted when IE is closed |
 |
P |
= |
Persistent |
Session cookies are treated just as Persistent Cookies are treated. |
 |
O |
= |
Overrides |
Per site settings override the Privacy
settings |
| ( I ) |
I |
= |
Ignored
|
Per site settings on the Privacy tab are NOT followed |
An earlier, slightly different version of this table was originally posted on the DSLR Security Forum by R2. |
Keep in mind that the table you see above is a somewhat simplified picture of IE 6.0's handling of cookies when the slider bar is used. We haven't even begun to discuss how IE 6.0 interprets the nitty gritty terms contained in P3P compact policies to distinguish "acceptable" compact policies (those that do not use "personally identifiable information" or use it with users' "consent") from "unacceptable" ones (those that do "use personally identifiable information" without "users' "consent"). (For details, see the "Unsatisfactory Cookies" section on
THIS page from Microsoft.)
Confused? Microsoft provides a few pages to explain all of these Privacy settings:
-- Configuring
Privacy Options
-- Privacy in Internet Explorer 6
-- Use Security and Privacy Features in Internet Explorer 6
My advice: take some aspirin before you wade in -- you'll need it.
- The Privacy Settings slider bar largely treats opt-in and opt-out policies the same. With but two exceptions, IE 6.0 regards both opt-in and opt-out provisions within compact policies as sufficient "consent" to classify the compact policy as "acceptable" or "satisfactory," even when "personally identifiable" information is used. This is a major concession to the online marketing and advertising industry inasmuch as it effectively values the commercial needs of marketers and advertisers over the privacy of web surfers. (The two exceptions are at the "High" level in first-party and third-party contexts, and the "Medium-High" level in third-party contexts.)
- The privacy levels used by Privacy Settings slider bar provide less useful control over third-party cookies than they could or ought to. The handling of cookies from major third-party advertisers and marketers like Doubleclick (who will almost always have "acceptable" compact policies) is especially problematic. With the Privacy Settings slider bar, there is no way to block these cookies (or even "downgrade" them to session cookies, rendering them worthless for the marketers involved) except by choosing the "Block All" setting, which for most users who surf the net is not a viable option. What Microsoft's reasoning for this arrangement might be is puzzling, as third-party cookies almost never provide web surfers with direct, substantive benefits; they are almost exclusively designed and used to benefit marketers and advertisers. (And, no, "personalized" advertising and direct marketing do NOT count as significant benefits to the end user or web surfer.) Moreover, third-party cookies from advertisers and marketers are precisely the cookies that privacy conscious individuals fret over the most-- these are the cookies that allow users' Internet activities to be tracked and monitored from site to site. Yet these are the very cookies that IE 6.0 most assiduously allows. To the skeptical, it would at least appear that IE 6.0's Privacy Settings slider levels were explicitly designed to protect the cookies of major third-party advertisers and marketers like Doubleclick. But, then, Microsoft never seemed to regard cookies as much of a problem in the first place.
- The Privacy Settings slider bar is but one of three different mutually exclusive ways to configure cookie handling in Internet Explorer 6.0 (the other two are the Advanced Privacy Settings and custom XML Privacy Import files). And there is the Per Site Privacy Actions list for individual web sites to consider. Most users will find the relationship between all of these settings confusing and murky. The easy way out, as we noted above, is the Settings slider bar, but this is probably the worst choice for those concerned with preserving both usability and online privacy. Users would be better off employing one of these alternative strategies for configuring cookie handling in IE 6.0.
- The Privacy Report provided for sites ( View >> Privacy Report... ), while helpful, still doesn't provide enough meaningful information about sites, cookies, and privacy policies. Most importantly, it doesn't report WHY it rejected some cookies and accepted others. Instead, web surfers are left to sift through complicated privacy policies and figure it out for themselves.
- IE 6.0 provides warnings when cookies are blocked, but not when they are accepted. This really is no surprise, as IE 6.0 "presents" the online world through the eyes of advertisers and marketers -- for them, it IS a problem when cookies are blocked (and surely you must think the same way, yes?). For privacy conscious individuals, however, blocked cookies are not a problem, but rather the goal. If you're concerned about your privacy, cookies are primarily a problem when they are accepted.
- IE 6.0 handles pop-ups and pop-unders in ways that are not protective of users' privacy. Pop-ups and pop-unders are often loaded in complete new windows. The sites loaded in these new windows are treated as first-party sites, even though the user never explicitly chose to visit those sites. As first-party sites, these pop-ups and pop-unders are treated more leniently by IE 6.0 than standard third-party sites. In effect, these pop-up and pop-under ads force first-party cookies on the user. The user did not choose to surf to the pop-up/pop-under ads' sites, yet those ads nonetheless load as a first-party sites and IE 6.0 accepts their cookies as a first-party cookies. Moreover, IE 6.0 also seems to have problems blocking unacceptable third-party cookies from sites loaded in pop-ups and pop-unders. The net effect of these flaws is to blur even further the distinction between first-party and third-party cookies -- which further emasculates the Privacy protection provided by IE 6.0's Privacy settings. (For more details on IE 6.0's problems with pop-ups and pop-unders, see THIS page.)
- While cookies can be easily blocked by adding web sites and domains to the Restricted zone, IE 6.0 provides no quick, convenient way to add sites to Restricted zone. Users must open the Internet Options box, navigate to the Security tab, and add URL's manually. Interestingly, you can download an add-on utility from Microsoft that will put "Add to Trusted Zone" and "Add to Restricted Zone" options on the Tools menu, but those options ought to be in the default interface -- without them, the Security zones are a pain to use.
- IE 6.0 removes cookie controls from the Trusted and Restricted zones (the Privacy settings discussed above apply to the Internet zone only). While cookie handling for sites in the Trusted and Restricted zones can be controlled, users must either resort to custom XML Privacy Import files to do the trick or hack the Registry. Given the complexity involved in performing either of these tasks, however, these are not viable options for the majority of users.
- Although the P3P standard is based on the notion that users should be able to specify the types of information they will disclose to web sites and the contexts under which they will do it, IE 6.0 doesn't provide users with a ready means to configure these types of information or the contexts (opt-in or opt-out). Instead, IE 6.0 uses two groups of information types -- "personally identifiable information" and "non-personally identifiable information" -- and assesses those groups as "acceptable" or "unacceptable" based on the existence or absence of "consent" ("explicit" or "implicit"), without ever providing users direct access to the underlying information types. (For a definition of "personally identifiable information" contained in compact policies that will cause a compact policy to be labeled "unacceptable" if no "consent" is present, see the "Unsatisfactory Cookies" section on THIS page.) Again, users can resort to custom XML Privacy Import files, but most users will find such a task beyond their means.
- The most effective control over cookie handling in IE 6.0 is provided by custom XML Import files, but IE 6.0 gives users no ready means to construct them through the Privacy settings interface. There is no way to query what settings the user's privacy preferences, no way to generate XML files based on those preferences, and no way even to report the settings that are currently in use. In short, IE 6.0 provides no assistance in using custom XML Privacy Import files beyond the poorly documented option to import them.
- IE 6.0's reliance on P3P compact policies strongly suggests that the mere existence of privacy policies is the most important standard in determining how privacy friendly a web site is. Thus, IE 6.0 paradoxically presents major advertisers and marketers like Doubleclick -- who will almost always have "acceptable" compact policies -- as more privacy friendly than small web sites that collect very little if any data at all about users but who don't have compact policies. Strange days indeed on the increasingly corporatized WWW.
- IE 6.0's P3P implementation provides no final guarantee that a site's published compact policy is in fact being followed. The P3P program is essentially a set of guidelines for publishing and interpreting Privacy Policies in a machine-readable format. Users have very few means to verify whether the stated policies are adhered to by web sites, nor is there any built-in mechanism to punish sites that do not abide by their own stated policies. It would be nearly impossible for any given user to prove exactly how and by whom their privacy had been compromised -- a task akin to finding out how one gets on spam lists.
- Because of this laxity and unaccountability, it is difficult, if not next to impossible, to locate a web site with a compact policy that IE 6.0 deems "unacceptable" at the default "Medium" slider setting. All web sites that we have encountered use "acceptable" compact policies. No site is willing to come out and declare that they are exploiting your privacy, and IE 6.0's definition of "satisfactory consent" allows them to get away with it. Since nearly all compact policies are "acceptable," IE 6.0's P3P implementation becomes little more than a hollow attempt to allay users' concerns for their online privacy rather than a concrete attempt to actually protect their privacy.
- In sum, IE 6.0's default privacy settings do not provide strong privacy protections to users. Furthermore, its implementation of P3P is muddleheaded and much too complex, forcing users to puzzle over too many new terms (compact policy, 1st-party vs third-party, leashed cookies, session cookies, downgraded cookies, et al) and confront too many complicated, murky, poorly explained options. Rather than empowering users, IE 6.0 actually makes the task of protecting one's privacy online even more difficult and complicated.
Doubt me? check out the following discussion threads from the DSL Reports Security forum, where a bevy of dedicated users worked for more than a month (in over 360 posted messages) to make sense of IE 6.0's Privacy settings:
-- "IE6 and Cookies"
-- "IE6 does not handle cookies the same"
Then read THIS page and THIS page from the W3C, which detail the standards for P3P compact policies and explain how they are deployed. But of course you'll also have to read
THIS page from Microsoft, which lays out how those P3P standards are implemented in Internet Explorer 6.0's Privacy settings. You probably also ought to read THIS page and THIS page as well, just to make sure you're clear on key terms and descriptions. And don't miss THIS page for tips from Microsoft on how to put together custom XML Import files for use with IE 6.0.
If you do plunge into Microsoft's documentation, you have my sympathies. I think you'll find that Microsoft's documentation is not only murky and confusing, but just plain WRONG in at least two cases. See the description of the five slider bar levels on THIS page, which is admittedly out of date. And see the description of the "Low" setting on THIS page, which specifies "Deny" for third-party cookies without compact policies, whereas every other Microsoft source, including the actual IE 6.0 Privacy tab, specifies "Downgrade." Apparently even Microsoft can't keep IE 6.0's slider bar settings straight. (Credit goes to R2 for catching this "Low" setting discrepancy.)
While the new Privacy settings in IE 6.0 do provide users with a more finely grained set of options for controlling cookies, the vast majority of IE 6.0 users will find these options much too confusing and involved to be of any real use. Problematically, the default Privacy settings of IE 6.0 are simply too lax for users to expect any meaningful improvement in the protection of their online privacy by IE 6.0 straight "out-of-the-box." Still worse, not only does IE 6.0 largely treat opt-in and opt-out compact policies the same, but IE 6.0's P3P-based Privacy Settings make it next to impossible to block cookies from major third-party advertisers and marketers.
Given these lax default Privacy settings, the scandalous treatment of opt-in and opt-out policies, the inexcusable provisions built in for third-party advertisers, as well as the confusion and frustration most IE 6.0 users will likely experience when confronted with these new settings, IE 6.0 arguably represents a step backwards in the struggle to offer internet users a reliable way to ensure their online privacy. Indeed, when these serious flaws are considered along with Internet Explorer's well-known ActiveX security problems as well as its support for Browser Helper Objects and other dangerous "spyware" customizations, Internet Explorer 6.0 could well be regarded as the premier direct marketing platform for online advertisers -- and a privacy nightmare for typical home users and web surfers.
In light of the sheer complexity of the P3P specification as well as IE 6.0's idiosyncratic way of classifying and sorting the P3P compact policies of individual web sites, many IE 6.0 users will find that the simplest and most effective way to guarantee their privacy is to avoid IE 6.0's P3P-based cookie settings altogether. Once users have dispensed with IE 6.0's P3P-based configuration options, they can turn to more effective methods to protect their privacy.
|
Alternatives to the P3P-based Slider
Bar in IE 6.0
To protect your privacy in Internet Explorer 6.0, you should reject the Privacy Settings slider bar and use some alternative strategy to configure cookie handling. Any of the following strategies will give you better privacy protection than the slider bar, while still allowing you to visit your favorite web sites.
- Advanced Privacy Settings & Per Site Privacy Actions
Override the default Privacy settings with the Advanced Privacy Settings (both first-party and third-party cookies blocked). For trusted web sites that require cookies, add those sites either to the Per Site Privacy Actions box or the Trusted sites zone.
This strategy of "locking down" the Internet zone and then making exceptions for trusted sites is often called an "opt-in" strategy because by default you must explicitly add sites to the Per Site Privacy Actions box or Trusted sites zone before they can add cookies. When combined with tight Internet zone Security options (e.g., scripting, ActiveX, JavaVM, and other dangerous settings Disabled), this "opt-in" cookie strategy gives you a great deal of privacy while still allowing you to access trusted sites.
If you'd like step-by-step instructions on configuring Internet Explorer's Privacy settings (as well as its several other Security settings), see THIS page.
- Custom XML Privacy Import Files
Use a custom XML Privacy Import file. You can find a generous selection of such files in the XML-Menu package located HERE. All of these XML files give you greater control over IE 6.0's cookie handling in the Internet zone as well as the Trusted sites zone. As with the previous option, trusted web sites that require cookies can be added either to the Per Site Privacy Actions box or the Trusted sites zone.
You can import XML files from the Internet Options Privacy tab by hitting the "Import..." button. See the ReadMe for XML-Menu for more details on using custom XML Privacy Import files.
- Restricted Sites Block Lists
Download and install a custom block list to load known advertisers, marketers, and purveyors of spyware into the Restricted sites zone (which blocks all cookies by default). You can find such a block list HERE.
A block list of Restricted sites can be a useful option if you'd rather not "lock down" the Internet zone and Privacy settings (which can lead to problems with some web sites), but still want to protect yourself from major third-party advertisers, marketers, and spyware pushers.
You might also consider using a custom-built HOSTS file, such as the one maintained by hpguru.
- Third-Party Filtering & Blocking Software
Use free, third-party filtering software, such as ad blockers, cookie crushers, and pop-up stoppers. You can find a long list of such programs HERE.
If you employ a third-party filtering/blocking program to handle cookies, you will find it simplest to configure IE 6.0 to allow all cookies and let that third-party application handle cookies exclusively, not IE 6.0. Although you can use a third-party filtering program in conjunction with IE 6.0's cookie handling options, it is simpler to rely on one program or method alone in order to avoid confusion.
All of these strategies provide simpler and more reliable ways for users to protect their privacy while surfing the web than the P3P-based Privacy Settings slider bar.
|
The bottom line is that P3P is yet another attempt to push the mere existence of privacy policies as evidence that little is amiss in the online corporate playground. Microsoft and other like-minded companies and organizations may trumpet the existence of IE 6.0 and all these P3P compact policies as further proof that citizens and consumers are being offered substantive choices that protect their online privacy. As we've seen above, though, these "choices" are bad ones, if only because they are too unwieldy to be taken advantage of, even by the most savvy of web surfers. For
typical home PC users -- who have little to no hope of ever making heads or tails of IE 6.0's Security zones and Privacy settings -- these "choices" effectively amount to no choice at all. Still further, this system of "choices" breaks before we even begin considering whether these privacy compact policies can be trusted absent clear legal enforcement mechanisms, or whether the uniformly exploitative behavior detailed in so many of those policies represents the kind of "choice" worth having.
Sadly, the net effect of P3P and IE 6.0 for 99% of web surfers will be nil. Whether blissfully unaware of what is going behind their backs or too confused to do much of anything about it, most web surfers will see no change in their online "experience." The cookies will continue to be set, the data about their online behavior will continue to flow, and the
corporate lobbyists in Washington will ever more joyously extol the effectiveness of industry self-regulation.
For other critiques of IE 6.0 & P3P, check these pages:
And for downloadable files to configure Internet Explorer 6.0's
Privacy settings, see these pages:
Special thanks to R2 for reviewing this section on IE 6.0, going
over the relevant documentation from Microsoft one more time, and providing
several critical observations about privacy problems in Internet Explorer 6.0.
Any factual or interpretive errors, however, are my fault alone.
No Guarantee of Privacy
Fifth, a privacy seal on a web site is no guarantee that the site does not engage in privacy invasive or abusive practices. Let me repeat: that a web site has a privacy seal from one of the big privacy seal programs like TRUSTe, BBBOnline,
ESRB, NAI,
DMA Safe Harbor, or CPAWebTrust does not mean that the web site is privacy friendly. All that privacy seal means is that the site has a "Privacy Policy" of some sort posted, and that the web site abides by the terms set forth in that "Privacy Policy." What that "Privacy Policy" consists of is by and large left to the site itself.
Whether a web site has a privacy seal or not, researchers have found, "your privacy is assured -- of being invaded." In fact, sites with privacy seals are more likely to be privacy invasive than sites without privacy seals. (See also THIS page for a harsh critique of TRUSTe.)
Despite years of education efforts (or rather perhaps because
of years of corporate PR efforts), most Americans still believe that the existence of a privacy policy on a web site means that the site will respect their privacy and not share or trade personal information collected about them. See this recent report (PDF document) by the Annenberg Public Policy Center for the depressing details. And see this
report, which explains why asymmetric information (i.e., a situation in which the companies know more than consumers) means that privacy policies and seal programs lead to a "lemons market" in privacy protection.
This confusion is in part attributable to the sheer unreadability of most of these corporate privacy policies. Reuters neatly summarized the problem identified by the Annenberg Public Policy Center Report thusly: "The dense, legalistic documents that many commercial Web sites post to explain their data-collection habits are more likely to provide false reassurance than clarity to Web surfers." (1) (See also THIS critique of "obfuscation in gobbledygook privacy policies."
THIS interview also has useful information about the readability of privacy policies. THIS study identifies the same unreadability in financial privacy policies.)
And just what do those much-touted "Privacy Policies" actually say?
Not what you'd think. Those companies and organizations who maintain that your privacy is safe in private hands are manifestly NOT interested at all in protecting your privacy (see THIS page for a list of names, many of which are gallingly deceptive). Indeed, many of them have business models that are explicitly designed around the exploitation of your privacy. And their "Privacy Policies" ought to tell you as much. What most of them boil down to is this:
We value your privacy. To that end...
- We will collect massive amounts of data about you.
- We will employ whatever technological means necessary to collect these data.
- We will use these data however we damn well please.
- We will share, exchange, or sell these data only to/with "select business partners" (viz., whomever we damn well please).
- We have no responsibilities or obligations to respect you or your privacy.
- You have every responsibility and obligation to respect us and our intellectual property.
- All our intellectual property is exclusively protected by our fleet of attorneys.
- All your data are belong to us.
- This is all for your benefit, and there's nothing you can do about it. If you entertain any fantasy of doing something about it, we will
sue the begeezus out of you.
- Now, would you kindly accept a few cookies and then give us your name, SSN#, email address, street address, place of employment, phone number, credit card number, and ZIP code?
|
Whatever else such policies might be, they cannot be called, properly speaking, "Privacy Policies"; they would be more accurately labeled "Exploitation Policies." Such policies, even when accompanied by third party "seals," are
next to worthless as privacy guarantees. That should come as no surprise because most of these privacy policies were
never designed to reign in corporate misbehavior, as Junkbusters notes on its web site:
| We call a privacy policy vacuous if there is nothing that it stops the company doing. A vacuous policy is like a pseudo-scientific theory that cannot be falsified by any empirical evidence. Vague statements such as ``we strive to consider our valued customers' preferences'' reassure only the gullible. Of course most privacy policies are the product of PR people and lawyers, so they are made to sound nice while exposing the company to absolutely no risk no matter how badly it behaves. (Junkbusters - "Privacy Policies") |
Or, as EPIC succinctly puts it in the title to their report on Internet privacy: Notice Is Not Enough. (See also THIS
privacy policy, which is a parody --but only just barely -- of what currently passes for privacy policies on corporate web sites.)
To help you understand just what these "Privacy
Policies" mean, take a look at this example privacy policy from online
giant Yahoo!:
| Yahoo!
Privacy Policy (http://privacy.yahoo.com/) |
Comment |
| |
|
| Yahoo! takes
your privacy seriously. Please read the following to learn more about
our privacy policy. [...]
|
This is the
standard, vapid claim about valuing your privacy. Of course, nothing in
what follows accords with this "commitment," except where
Yahoo! has been compelled by force of law to respect your
privacy. |
| Information
Collection and Use
General
- Yahoo! collects personal information when you
register with Yahoo!, when you use Yahoo!
products or services, when you visit Yahoo! pages or the pages
of certain Yahoo! partners, and when you enter promotions
or sweepstakes. Yahoo! may combine information about you that we
have with information we obtain from business partners or other
companies.
- When you register we ask for information such as
your name, email address, birth date, gender, zip code, occupation,
industry, and personal interests. For some financial products and
services we may also ask for your address, Social Security number,
and information about your assets. Once you register with Yahoo! and
sign in to our services, you are not anonymous to us.
- Yahoo! collects information about your transactions
with us and with some of our business partners, including
information about your use of financial products and services that
we offer.
- Yahoo! automatically receives and records
information on our server logs from your browser, including your IP
address, Yahoo! cookie
information, and the page you request.
- Yahoo! uses information for the following general
purposes: to customize the advertising and content you see, fulfill
your requests for products and services, improve our services,
contact you, conduct research, and provide anonymous reporting for
internal and external clients. [...]
|
The company gathers quite a bit of sensitive
information...
...and, of course, it's all for your benefit. These
companies are almost never honest about what they themselves stand to
gain from such practices. |
Information
Sharing and Disclosure
- Yahoo! does not rent, sell, or share personal
information about you with other people or nonaffiliated companies
except to provide products or services you've requested, when we
have your permission, or under the following circumstances:
- We provide the information to trusted partners
who work on behalf of or with Yahoo! under confidentiality
agreements. These companies may use your personal information to
help Yahoo! communicate with you about offers from Yahoo! and
our marketing partners. However, these companies do not have any
independent right to share this information.
- We have a parent's permission to share the
information if the user is a child under age 13. Parents have
the option of allowing Yahoo! to collect and use their child's
information without consenting to Yahoo! sharing of this
information with people and companies who may use this
information for their own purposes;
- We respond to subpoenas, court orders, or legal
process, or to establish or exercise our legal rights or defend
against legal claims;
- We believe it is necessary to share information
in order to investigate, prevent, or take action regarding
illegal activities, suspected fraud, situations involving
potential threats to the physical safety of any person,
violations of Yahoo!'s terms of use, or as otherwise required by
law.
- We transfer information about you if Yahoo! is
acquired by or merged with another company. In this event,
Yahoo! will notify you before information about you is
transferred and becomes subject to a different privacy policy.
|
This passage
is cleverly worded. Notice how it leads off with strong denials, but
then chisels away at those denials until almost nothing is left.
And here is the standard "trusted partners"
bit. Who are "trusted partners"? Anybody the company chooses
to do business with. Can you seriously imagine a company sharing such
information with any other business or organization that wasn't a "trusted partner"?
As you might have suspected, all bets are off if the
company is swallowed up by another entity. |
- Yahoo! displays targeted advertisements based on
personal information. Advertisers (including ad serving companies)
may assume that people who interact with, view, or click on targeted
ads meet the targeting criteria - for example, women ages 18-24 from
a particular geographic area.
- Yahoo! does not provide any personal
information to the advertiser when you interact with or view a
targeted ad. However, by interacting with or viewing an ad you
are consenting to the possibility that the advertiser will make
the assumption that you meet the targeting criteria used to
display the ad.
- Yahoo! advertisers include financial service
providers (such as banks, insurance agents, stock brokers and
mortgage lenders) and non-financial companies (such as stores,
airlines, and software companies).
|
Yahoo! is
loaded with third-party advertising, and most (if not all) of this advertising is
based on the opt-out principle. Even though these companies are
confident that you'll love being direct marketed into the ground, they
refuse to acquire your explicit consent first. |
Cookies
- Yahoo! may set and access Yahoo! cookies
on your computer.
- Yahoo! lets other
companies that show advertisements on some of our pages set and
access their cookies on your computer. Other companies' use of their
cookies is subject to their own privacy policies, not this one.
Advertisers or other companies do not have access to Yahoo!'s
cookies.
- Yahoo! uses web
beacons to access Yahoo! cookies inside and outside our network
of web sites and in connection with Yahoo! products and services. [...]
|
Yahoo! will serve you up a generous helping of
cookies, many of them from third-parties.
Another standard dodge pioneered by Microsoft.
"Web beacons" are in fact web
bugs, but Yahoo! doesn't like the unsavory implications of the
term, so it dips into the deep well of corporate-speak and comes up with
this vacuous replacement. |
| Your
Ability to Edit and Delete Your Account Information and Preferences
General
- You can edit your Yahoo!
Account Information, including your marketing
preferences, at any time.
- New categories of marketing communications may be
added to the Marketing Preferences page from time to time. Users who
visit this page can opt-out of receiving future marketing
communications from these new categories or they can unsubscribe by
following instructions contained in the messages they receive.
- Certain communications from Yahoo!, such as service
announcements, administrative messages and the Yahoo! Newsletter,
are considered part of Yahoo! membership and you may not opt-out of
receiving them.
- You can delete your Yahoo! account by visiting our Account
Deletion page. Please click
here to read about information that might possibly remain in our
archived records after your account has been deleted.
|
Yahoo!
generously allows you edit your marketing preferences. (And they
are "marketing preferences" not "privacy
preferences.")
Notice, though, how Yahoo! reserves the right to reset
your preferences should they become too inconvenient. In such cases,
you'll have to "opt-out" all over again, because the company
simply won't take "No" for an answer. (Note: the Attorney
General of NY recently sued
Yahoo! to teach the company the meaning of "No.") |
Changes
to this Privacy Policy
- Yahoo! may update this policy. We will notify you
about significant changes in the way we treat personal information
by sending a notice to the primary email address specified in your
Yahoo! account or by placing a prominent notice on our site.
|
What little the company did commit to doing to protect
your privacy is hereby
summarily
withdrawn. |
Questions
and Suggestions
|
Of course the company is TRUSTe-certified!

And you thought that privacy seal actually meant
something! |
This kind of "privacy policy," unfortunately, is all too typical of the offerings from major companies.
- For an analysis of EULAs and Privacy Policies used in "crapware" applications, see THIS discussion at DSLR/BBR.
- And see THIS guide to reading privacy
policies, as well as THIS
guide to navigating the fine print.
- And for an outstanding analysis of the EULA used by
Gator/Claria, see Ben Edelman's write-up HERE.
- Ben Edelman has still another excellent comment on
exploitative licenses HERE.
As examples of "self-regulation," such "privacy policies" certainly aren't adequate substitutes for substantive privacy protections written into law and enforced by strong civil and criminal sanctions. As we noted when discussing privacy seal programs earlier, the problem with "self-regulation." is the very basic conflict of interest which lies at the heart of such arrangements: there is simply too much money to be made from the exploitation of personal data for the industry to be entrusted with protecting the privacy of online users. Personal data translates quite directly into commercial revenue.
It should come as no surprise, then, to learn that, despite several years worth of efforts on the part of private industry to cobble together a regime of "self-regulation," this effort has been a massive failure. Not only does the corporate appetite for personal data appear to be increasing, but the few (and weak) self-regulatory policies which have been propagated by and within the industry are not even widely or consistently followed (see EPIC and Junkbusters for more information on the outright failure of "self-regulation"). Yet
companies continue to spin
their privacy policies and seals to unwitting consumers as misleading evidence that they're actually interested in protecting consumers' privacy. "Self-regulation" means only that companies can continue their privacy invasive practice while fooling consumers into thinking that their privacy is safe in corporate hands.
(It doesn't have to be this way, by the way -- see HERE.)
The abject failure of privacy policies to protect consumers'
private information is neatly highlighted by the JetBlue fiasco. Despite strong guarantees to the contrary, JetBlue happily handed over customer information on millions of its passengers to a Defense Department contractor working on a project for the Transportation Safety Agency (TSA), which administers the Computer Assisted Passenger Pre-screening System II (CAPPS II) program. For the sorry details see these news stories: 1,
2, 3,
4,
5,
6.
It turns out that JetBlue wasn't the only guilty party: after initially denying
that it had done so, Northwest fessed up to
doing the same thing with data on millions of its own passengers despite its privacy policy (1,
2) .
Still later it was revealed that American Airlines had
joined
in the fun as
well, making mince meat of its privacy
policy. All of this has come to nought, though, esp. after a court ruled
that privacy policies largely unenforceable
as contracts.
In sum, the key to understanding corporate privacy policies is to recognize them for what they are: public relations efforts, not serious attempts to regulate or control corporate business practices.
Not only are privacy policies largely unenforceable
as contracts, but privacy policies may not even represent actual practices. A recent article (p.1, p.2) in The New York Times succinctly put the situation this way:
Janice Abrahams, a Web site designer who runs www.privacyparts.com, a site devoted to online privacy practices, recently gave up after weeks of trying to create a page that would identify online services by their privacy practices. "I feel like I've been nailing Jell-O to a tree -- with my head," she said.
What is going on at many Web sites is no mystery to Penn Gillette, the magician and former technology columnist for PC Computing Magazine, which is now defunct. The choice offered is no choice at all, he said, gently coerced before or after the fact in what is known as a "force" or a "magician's choice." As a rule of thumb, when someone asks you to pick a card, any card, he said, "if the guy is wearing a top hat, he's not giving you a real choice." |
Despite the spread of privacy policies online, the online privacy situation has not
improved, with around 50
percent of large companies still sharing customer data with other entities without
seeeking permission. This sorry history of broken promises is all of a piece with the history of technology and privacy, as one expert explained to The New York Times (1):
Aviel D. Rubin, the technical director of the Information Security Institute at Johns Hopkins University, said that every new technology with the potential to invade privacy was introduced with pledges that it would be used responsibly.
But over time, he said, the desire of law enforcement and business to use the data overtook the early promises.
"The only way to get real privacy," he said, "is not to collect the information in the first place." |
Excuses, Excuses...
Opponents of sound privacy legislation offer any number of excuses and reasons for the unnecessity and inadequacy of privacy regulations. These excuses simply do not stand up to critical scrutiny.
You can find a succinct summary of the reasons that their excuses don't hold up at Junkbusters in an article by Jason Catlett (founder and President of Junkbusters) titled, "Six Silly Excuses for Postponing Privacy Rights". I excerpt here the most relevant parts of this prescient piece:
Excuse: "The federal government is a prime violator of privacy, therefore the federal government shouldn't legislate on privacy."
As silly as saying: "The Department of Defense (or the IRS or the FBI) have done a lot of bad things, therefore the government shouldn't be involved in laws about murder or property rights."
Privacy legislation should create rights for individuals, not huge governmental agencies. The Telephone Consumer Protection Act of 1991 took exactly this approach: give individuals the right to sue for $500 any marketer who calls them at 3am.
|
Excuse: "Market forces and media scrutiny are enough to force companies to respect privacy. Privacy will become a competitive weapon."
As silly as saying: "Market forces will stop companies polluting. Vigilant reporters will expose and stop abuses by the telemarketing industry. Class action suits and 'seals of approval' make consumer product safety laws unnecessary. Safety will become a competitive weapon in the airline industry. The FAA isn't needed because passengers won't fly on airlines that frequently crash their planes."
Economists use the name "negative externality" for a downside that isn't accounted for in the market, and know it can't fix them alone.
|
Excuse: "Privacy legislation would be bad for the economy."
As silly as: "The emancipation of slaves would be bad for the economy" or: "Regulation would ruin the consumer credit business."
The credit bureaus tried this line 30 years ago, were overruled, and were proved 100% wrong. It's also as silly as saying that creating an Environmental Protection Agency would ruin the chemical business or the oil business.
On the contrary, surveys now routinely show that the number one factor limiting growth in ecommerce is that people fear they have no recourse if their personal information is misused. Consumer confidence from legally guaranteed rights will grow the market, not shrink it. The $50 limit on credit card liability didn't destroy the industry, it enabled it. |
Excuse: "The Internet is international, so there's no point having privacy laws."
As silly as: "The Internet is international, so there's no point having copyright laws (or patent laws or taxation laws)."
Wrong. Companies have sought and obtained strong protection against copyright infringement. Consumers should have strong protection against privacy violation. |
Excuse: "Technology is too difficult for the government to understand. They can't get it right."
As silly as: "Technology is too complex to be understood by the US Patent Office, or the Pentagon, or the President, or the people of the United States."
Such technocratic arrogance is deeply offensive to the democratic values of this country. It's also directly contradicted by recent experience: the Federal Trade Commission's 100-page rule for the Children's Online Privacy Protection Act of 1998 was widely praised by privacy advocates and trade groups alike. |
Excuse: "It's already too late to save privacy. There's already so much data about us we have lost all hope of control forever."
As silly as: "The environment is already too damaged by pollution."
The Great Lakes got cleaner this decade. We can get privacy back within a decade or two.
But because of technology, privacy no longer happens as an accidental byproduct of the obscurity of manual records. In the next century we're not going to get much privacy unless we have privacy rights, and that requires a law. We've got to get this right, or we will have let a fundamental liberty lapse. Who says we can't afford privacy? That's like saying we can't afford freedom.
|
I think we can add yet another excuse that simply cannot withstand critical scrutiny:
Excuse: "Governmental protection of the integrity of consumers' privacy by regulating the collection, use, sale, and exchange of data about individuals would be a violation of free speech."
As silly as saying: "Governmental protection of the integrity of companies' 'intellectual property' by regulating the collection, use, sale, and exchange of their inventions, expressions, brand names, and logos through the granting of patents, copyrights, and trademarks would be a violation of free speech."
We have long recognized the propriety of regulating commercial speech, and regulation of the collection, use, sale, and exchange of private consumer data by companies would be little different. Still further, we must wonder at those who would go to the wall to defend the intrusion of governmental regulation into the marketplace when it serves the interests of corporate intellectual property (government granted monopolies) but who somehow bristle at the prospect of the government's intervening to protect the private data of consumers.
Sad to say, when most "free market" advocates say they are strictly opposed to governmental interventions into the marketplace, they are being less than honest. In fact, what they really mean is that they oppose governmental intervention when it doesn't protect the interests of corporations. In those cases where governmental action does serve to protect corporate interests, they are only too happy to entertain governmental intervention into the marketplace, and they will beat a path to the PTO (Patent & Trademark Office),
U.S. Copyright Office, and the United States Congress to secure it. |
"But They Have a Choice..."
Corporate apologists often reject strong legislation to protect citizens' online privacy by insisting that Internet users have a choice. Web surfers freely choose to visit web sites they visit -- it is said -- and they can just as easily choose not to visit web sites whose privacy practices they find objectionable. Thus, we find the friends of Corporate America making blithe, airy pronouncements like the following:
Users who are worried about revealing personal information can set their browsers not to accept cookies. All modern browsers provide some sort of cookie management capability that allows users to refuse them all, decide which to accept, or block them by site. There are also several tools on the market that make it easy to read and edit cookies.
To the extent cookies present a privacy problem at all, it is a problem that will vanish as consumers learn how their computers work. Cookies are a privacy issue in the same way that window drapes are a privacy issue. Consumers who want sunshine open the drapes. Consumers who want privacy close the drapes. Consumers who want customization accept cookies. Consumers who want privacy do not accept cookies. ( Privacilla. "Cookies." ) |
This is a narrow, cramped, and even naive understanding of "choice" -- one that ignores any number of problems with the "choices" being offered:
- This understanding of "choice" assumes that consumers know and understand the arcane privacy policies of web sites, which often hide critical disclosures behind a blizzard of arcane terminology. When users can't understand the "choices" being offered, that's not "choice."
- It assumes that users have a healthy, working knowledge of how their Internet software interacts with web sites, the wealth of data that software allows web sites to gather, and the kinds of exploits that web sites can use to insert direct marketing mechanisms such as "spyware" and "foistware" onto their computers. Still worse, some companies like AOL have even taken it upon themselves to make "choices" for computer users -- by adding their own web sites to Internet Explorer's Trusted sites zone, for example, or using other means to bypass users' actual configured choices. Most users have very little understanding of how to prevent their Internet software from being used against them, or even to recognize when web sites have converted their own operating systems and web browsers into fancy direct marketing trojans. When users aren't in control, they don't have "choice."
- It assumes that users have some reliable means to verify web sites' declared privacy practices, when in fact they don't. Absent strong provisions for legal enforcement, web sites' privacy policies represent little more than empty public relations campaigns. Until Corporate America stops treating personal privacy as a public relations problem and users acquire the legal means to verify and enforce web sites' privacy practices, they don't have "choice."
- It assumes that users can count on web sites' consistently abiding by their stated privacy policies. But that isn't true. As we noted earlier, the current legal climate allows web sites to change their privacy practices without warning and with every expectation that there will be no legal sanctions whatsoever. When web sites rip the rug out from under consumers who based their "choices" on privacy policies that later become too inconvenient -- whether during normal business operations, acquisition and takeover, or bankruptcy -- then Internet users don't have substantive "choices" that they can rely upon.
- It assumes that Internet users can recognize and stop potential privacy violations before their privacy is seriously compromised. In fact, with the exploding use of "spyware" and "foistware" by direct marketing companies, users often don't sense anything wrong until the damage has already been done. And even after their computers have been trashed and their personal data looted, most users have little idea how to clean up the mess and take back their computers -- and their privacy. When normal computer users can't prevent intrusions on their privacy from commercial interests that won't hesitate to hijack their computers (and who have the technological means to do it), then "choice" becomes a moot issue.
- It assumes that standard market mechanisms to relay consumers' "choices" back to suppliers work properly when consumers aren't even aware of the privacy invasive practices they're being subjected to and aren't in any position to stop them when they do. But that is absurd. What suppliers of content, software, and services so often see in the market is not the result of the "choices" being made by consumers, but rather the success of their own attempts to hide their privacy abusive practices from consumers. Yet the current market climate encourages and rewards such behavior, which effectively sidesteps the issue of consumer "choice." When online purveyors of "spyware" like Brilliant Digital Entertainment can sneak millions of copies of its "foistware" onto consumers' computers, that says nothing about the "choices" that consumers have made -- it only tells us that the market is broken.
- It assumes that personal privacy is so little valued in our society that a "lowest common denominator" approach is a tolerable level of protection. As a society, though, we long ago decided that this kind of "wild west" environment was simply unacceptable when things like health, education, financial welfare, consumer protection, environmental protection, and civil rights were on the line. Moreover, we provide strong protections for the sensitive data of commercial interests in the form of intellectual property rights and laws governing business trade secrets, and there is no good reason not to extend similar protections to private individuals as well. Personal privacy is just as critical to citizens and consumers, but in an economic and business environment that encourages a race-to-the-bottom most "choices" that are being offered them aren't "choices" worth having.
- It assumes that viable "choices" are even being offered online. Corporate lobbyists sternly lecture any and all that privacy will become an important selling point in the "free market" of competing corporations and web sites. But where are these web sites and companies? Anyone who has surfed the Net will tell you that it is nearly impossible to use the web with cookies turned off, for example, or even to disable such dangerous active content as Java, ActiveX, and scripting. Too many web sites require these technologies for web surfers to seriously consider disabling them, even though some of these technologies can represent serious computer security threats. The few choices that are left in this area are likely to further erode as corporations extend their control over the Internet and strengthen their ability to set the terms and conditions for access to it. Bottom line: the "choices" that corporate apologists insist are being offered (or soon will be -- hey, they're always just around the corner!) simply aren't there.
- Finally, though, this issue of "choice" assumes that the question of who initiated contact with whom is some kind of important ethical and legal distinction. In fact, it is a dodge. Apologists for Corporate America protest that it is consumers who initiate contact with web sites and that they have the choice not to visit those web sites. But ask them if that distinction then means that they support laws protecting consumers against unsolicited bulk commercial email (i.e., spam) -- situations where it is businesses who initiate the contact, not consumers -- and they will oppose those laws as well. The issue of "choice" was and is merely a clever political gambit to preserve a legal environment that enables corporations to work on ensuring that consumers ultimately have no choice at all.
Gator Corporation, one of the biggest "crapware" pushers on the Net, gave the whole game away when it proposed a set of industry self-regulatory measures that it called "Online Advertising 'Rules Of Engagement." You only need "rules of engagement" when you've declared war on hapless enemies who have no real means of defending themselves. And like many other marketing or advertising entities on the Net, "crapware" pushers typically try to hide behind dense, obscure EULAs, Terms of Service, and Privacy Policies that they know most users will not read or even be able to understand.
|
When "Crapware" Strikes...
Not satisfied with the choices that netizens have been making, many online marketing firms and "entrepreneurs" have decided to take things into their own hands and make satisfactory "choices" for consumers. They do this by surreptitiously installing privacy invasive "spyware" and "foistware" -- in sum, "crapware" -- onto consumers' computers.
Once installed, such "crapware" can be used to monitor PC and Internet use, gather personally sensitive data, send those data back to direct marketing firms, serve up advertising directly to the users' desktops based on those data, and trojanize users' web browsers (almost invariably Internet Explorer) such that the web browsers become little more than bloated direct marketing tools. What kind of "choices" are consumers making when such "crapware" uses one or more of the following tactics?
- Stealth/Rogue Installation
automatically installs with little notice or warning when users visit "crapware"-infested web sites with active content options enabled, as many sites require them to be (and, yes, "crapware" entrepreneurs consider this sufficient "consent");
tricks users into installation by the use of deceptive buttons and hyperlinks, false error boxes and system
notices, uncloseable popups, or other
confusing GUI elements;
falsely poses as Microsoft Windows Update software, "anti-spyware"
software, or other software that may be desired by users;
uses known "malware" such as the W32.DlDer.Trojan and/or exploits known security holes in Internet Explorer and Windows to install on users' systems and reconfigure users' systems;
piggybacks on other host applications and web sites which install the accompanying "crapware" modules -- even when users uncheck the appropriate boxes and decline the installations -- and often provides no visible means to opt-out of the "crapware" installation alone;
uses frequently changed/morphed installers and installation methods to avoid
detection by "anti-crapware" applications such as SpyBot Search & Destroy and Ad-aware;
- High Pressure Installation
foists itself on users by piggybacking on other host applications which require installation of that "foistware";
uses scare tactics (e.g., displays of users' drive contents, IP addresses, or
browser headers; opening the CD-ROM drive) to exploit users' fears and pressure
them into installation;
is required by ISP's in order to provide "member content" and "connection maintenance" to users (who are already paying rising costs for their internet connections);
installs along with drivers for hardware and is required for proper functioning of that hardware, or installs as part of a BIOS/CMOS software package;
- Stealth Execution
configures itself to automatically launch and run silently in the background every time Windows or Internet Explorer start without notifying users or seeking their knowing consent;
obscures or hides its execution and behavior from users and "anti-crapware" utilities;
- Rogue System Reconfiguration
reconfigures users' systems to allow itself unfettered access to the Internet and allow "crapware" servers uninhibited access to users' computers;
hijacks users' web browsers to drive users to unwanted web sites and search services by making undesired system customizations and locking users out of the settings that would allow them to restore their browsers to a preferred state;
adds unwanted or unsolicited toolbars, searchbars, and other custom plug-ins or add-ons to the users' browsers or systems;
replaces critical Windows system files, thus interfering with the normal and proper operation of the users' systems and even imposing a system "death penalty" on the PCs of users who do attempt to uninstall it;
- Data Gathering
monitors users' use of their computers and the internet, collects usage data and other personally identifiable or sensitive data about users, and provides those data via a network connection to direct marketing and advertising companies;
- Backdoor Connectivity
establishes unannounced, unwanted network connections for the purposes of making unrequested updates to the software and users' systems or supplying data to interested parties;
makes unauthorized dial-up connections to 1-900 numbers without users' full understanding and consent;
- Obfuscation
buries key notices, terms, and conditions in complex EULAs and Privacy Policies that few consumers can make any sense of;
provides insufficient notice of installation, data gathering, backdoor connectivity, system reconfiguration, or other undesirable behavior;
- No Choice (Opt-Out/In)
won't take "no" for an answer because it provides no readily available means to opt-out of (let alone opt-in to) privacy invasive data gathering, system reconfiguration, and/or system updating for good;
demands that consumers to agree to outrageous terms & conditions such as the acceptance of unannounced / unsolicited updates, renunciation of third-party uninstallation methods (i.e., the use anti-"crapware" utilities such as SpyBot Search & Destroy and Ad-aware), or the uninstallation of "conflicting" programs (i.e., anti-"crapware" utilities such as SpyBot Search & Destroy and Ad-aware).
- Uninstallation Countermeasures
provides no visible means for uninstallation and removal;
refuses to be uninstalled when the host application is uninstalled;
provides broken uninstallers or uninstallers that actually install more "crapware";
takes active measures to avoid being uninstalled by "crapware" removal utilities like Ad-aware and SpyBot Search & Destroy, blocks the download and installation of those utilities, and even silently uninstalls such utilities without the user's permission;
When online advertisers and marketers resort to such tactics, that should tell you that they don't much care for consumer "choice." And in its current state, the market happily rewards entrepreneurs who ignore and override consumer "choice."
Dealing with "Crapware"
If your PC has been hijacked by an online marketing firm or "crapware"
entrepreneur and you're trying to clean up the mess, your first stop ought to be Lavasoft's web site, where you can download and install Ad-aware, a free "crapware"-removal utility. Another excellent, free "crapware"-removal program is SpyBot Search & Destroy.
Both Ad-aware and SpyBot Search & Destroy work much like standard anti-virus programs, so if you're familiar with Norton AntiVirus or McAfee VirusScan, you shouldn't have any problem running Ad-aware and SpyBot Search & Destroy. Both utilities will scour you computer for all instances of "crapware" and offer to remove them for you. You might be surprised at what they find on your system. Ad-aware and SpyBot Search & Destroy are fast, effective, and easy to use. If you surf the Net a lot or frequently install "free" programs from the Net, an anti-"crapware" utility is a must-have program, just like an anti-virus program.
If you're currently dealing with a "crapware" infestation, swing by the
SpywareInfo Support Forums, where you can post a HijackThis! log of your system and knowledgeable users can give you step-by-step advice for removing unwanted "crapware" applications from your computer.
For general information on "crapware," you also ought to consider visiting one of these excellent sites:
Those web sites offer a wealth of tips and advice for dealing
with "crapware." And for links to still more information and software to deal with corporate "crapware," see THIS page and THIS page.
Finally, to protect yourself against corporate "crapware," you ought to consider locking down your browser, esp. if it's Internet Explorer. Two other excellent programs to help prevent "crapware" from ever being installed behind your back by obnoxious web sites are JavaCool's free
SpywareBlaster and SpywareGuard.
And this very web site offers two other ways to lock down Internet Explorer so that "crapware" pushers can't hijack your browser or install unwanted software
behind your back without your knowledge or permission:
| IE-SPYAD: |
A long list of known advertisers, marketers, and "crapware" pushers that can be added to the Restricted sites zone of Internet Explorer. Once this list is merged into your Registry, most direct marketers and "crapware" pushers will not be able to resort to the usual "tricks" (e.g., cookies, scripts, ActiveX controls, popups, et al) they use to track your behavior and push unwanted software on you while you surf the Net. |
| |
|
| Enough is Enough! |
A lockdown utility for Internet Explorer 5 and 6 that automatically and securely configures Internet Explorer's Privacy and Security settings to stop obnoxious "crapware" pushers and other pushy direct marketers. |
|
"You Thieves Will Destroy the Internet!"
After loudly insisting that users have choices to protect their privacy on the Internet, the friends of Corporate America should be happy to see Internet users actually
exercising those choices, one would think. But they're not. In fact, people who dare to protect their privacy and exercise choice by blocking cookies and ads (or even surfing with images or active content disabled, which has the same effect) are increasingly being branded content pirates, destroyers of the Internet.
Corporate apologists love to lecture users about the innocuousness of cookies, for example, going out of their way to pooh-pooh users' privacy concerns and even mock them for mistakenly attributing more power to cookies than they actually
have. There are many problems with these apologias for cookies (and online marketing tactics more generally), including:
- the conflation of privacy and security issues, thus setting up strawman arguments to refute;
- the way these apologists often address the most ignorant myths about cookies as though most critics of cookies actually believed them;
- the weak, questionable assumption that most cookies are truly useful when hard experience on the Net suggests they are not;
- the way these apologists seek to put the burden on web surfers to explain why they block cookies, not on web sites to explain what they're doing with them;
- the refusal by so many apologists to substantively address the documented abuses of privacy that we've seen over the past few years;
|
|
...and the list goes on. Apologists for aggressive online marketing often seem more content to ignore or misconstrue what doesn't fit their tidy world view of the commercial Internet rather than address the very real and serious issues that folks have with the direct marketing practices on the web.
The biggest problem with this argument against privacy-conscious web surfers, however, is the way it suggests that they will ultimately be to blame for the collapse of the "free" Internet. (We'll ignore, for now, the fact that Corporate America is diligently working to re-code the "free" Internet to turn it into one vast, proprietary, corporate playground through intellectual property law and closed broadband monopolies.) When apologists for web sites that use third-party cookies and other obnoxious direct marketing tactics suggest that web sites will go to a for-pay model if users and web surfers continue to block cookies and advertising, they are in effect arguing:
"If you don't let web sites exploit your privacy with ads and cookies, they'll go to a for-pay model."
This argument is usually coupled with the observation:
"If you don't like what a web site does, you're free not to visit that web site."
But this argument is less than compelling for any number of reasons.
| 1. |
It puts the burden of maintaining a useful, robust Internet entirely on users, surfers, and consumers. On this argument, no responsibilities are ever assigned to advertisers and marketers; evidently they have none. In effect, this response assumes that the conversation between consumers and web sites will be or ought to be a one way conversation. Why do corporations and web sites not bear any obligations and responsibilities here?
|
| |
|
| 2. |
In effect this argument says, "It's a free market; if you don't like a web site's privacy practices, you can go pound sand." In other words, "We have no ethical obligations to you, and if you don't like it, that's just your tough luck." Yet when consumers understandably react with the same attitude by blocking ads and cookies, the corporate apologists start prattling on about how consumers owe them and have ethical obligations to them -- namely to accept cookies and put up with obnoxious direct marketing tactics. But why would users, consumers, and web surfers regard these alleged obligations with anything other than the same disdain they've received from web sites? Again, the corporate web sites want a one-way conversation.
|
| |
|
| 3. |
If web surfers are blocking cookies and other obnoxious forms of direct marketing, it's because they don't trust web sites. And the corporations who lie behind these sites are themselves to blame for the mistrust that consumers increasingly have for their web sites. These web sites have pursued aggressive, privacy invasive practices for too long. Still worse, they often lied, evaded, spun, and dissembled the entire time they were doing it. No one ought to be surprised that they're reaping the rewards of their obnoxious practices -- namely, the loss of consumer trust. Yet these web sites are somehow shocked that consumers have started to react as they have. Instead of lecturing consumers about how they're destroying the Internet, commercial web sites ought to be trying to regain their trust -- and that does NOT mean posting vapid privacy policies and subscribing to toothless privacy seal programs. It means making substantive changes to their fundamental business practices.
|
| |
|
| 4. |
Most consumers have very little means of gaining hard, reliable, verifiable knowledge of web sites' actual business practices. By contrast we do have plenty of documented cases of the abuse of users' privacy and trust. Based on this (lack of) knowledge, the safest policy for web surfers to follow is to assume by default that their privacy and trust will be abused until web sites prove otherwise. Moreover, web sites need to demonstrate that there are concrete benefits to sharing information and placing trust. In other words, the burden is on web sites to prove their safety, trustworthiness, and usefulness, not on consumers to provide good reasons for their mistrust (which they already have anyway).
|
| |
|
| 5. |
The number of users blocking ads and cookies is a small percentage of users -- there are statistics suggesting the percentage is around 1-2%. Rarely is this fact admitted or discussed by those who seek to blame consumers for the collapse of dot.bomb/dot.con business models. Instead, they would have you believe the whole industry is on the rocks due to this small percentage of users. But it is an argument made in bad faith, much like the music industry's blaming its woes on file trading, all the while ignoring its own abusive, monopolistic pricing practices.
|
| |
|
| 6. |
The biggest reason sites are moving to for-pay models stems from the great dot.com collapse of 2000/2001, yet this argument seeks to blame consumers. We now know, however, that all too many of these dot.com's did themselves in through bad business decisions, poor-to-non-existent business plans, and participation in the industry's over-investment in the stock market bubble (itself driven by a fraudulent, over-hyped IPO market culture), not anything consumers did. If commercial web sites are feeling the pinch, they need to re-evaluate their own business plans, not put the blame on consumers who refuse to allow their privacy to be exploited. |
| |
|
| 7. |
This argument is just a new variation on the same old threat that the business community has always used to head off criticism and governmental oversight of its abusive practices: "If you don't allow us to X, we'll take all of our toys and go home," where X in the past has been:
- exploit consumers
- make unsafe products
- pollute the environment
- engage in anti-competitive practices (collusion, price-fixing, dumping, tying)
- swindle the old and the poor out of their life savings
- charge exploitative, usurious interest rates
- pay sub-standard, non-livable wages
- force employees to work in unsafe conditions
...et al.
|
| 8. | Finally, most folks who filter advertising don't necessarily regard the ad content itself as the problem; rather, they dislike what advertisers and marketers attempt to do with the advertising space they buy on web sites (e.g., cookies, ActiveX controls, auto-installing spyware, blizzards of popups and popunders, et al). The industry has been extremely aggressive in finding new, obnoxious ways to exploit advertising space and convert users' web browsers into little more than fancy direct marketing trojans, and many web surfers finally got the point where they said: "Enough!" The simplest way to take care of the problem is to block the advertisers themselves and cut the problems off at the root. |
|
|
Not every apologist believes every one of the arguments addressed above, but many apologists for direct marketing on the Net do engage in or assume these arguments.
These apologists can lecture all they want, but their lectures are misdirected: they ought to be scolding web sites for placing too little value on the privacy concerns of Internet users and treating those privacy concerns as a little more than a public relations problem. The bottom line is: most people who block cookies block them selectively because they do perceive substantive benefits to keeping a select few cookies. Moreover, they don't need to be lectured, hectored, and berated by apologists for online marketing -- the benefits are clear, immediate, and obvious.
I keep three cookies on my system -- all for sites that I regularly visit and
use. I keep those three cookies because I know and trust the sites, and I derive real, demonstrable benefits from keeping them. When people block most other cookies (or even all cookies), it's because they don't see any clear benefits to allowing them -- and that's the fault of the web sites, not the web surfers.
And users certainly shouldn't be badgered to enable active content (crucial
to pop-up ads and other obnoxious advertising gimmicks), as active content (esp. ActiveX) is a well-known security hole through which crapware pushers, browser hijackers, and other nefarious elements of the web can trash users' computers.
Corporate apologists' lecturing users on why they need to accept cookies and not
block ads when the users don't see any clear benefits to doing so is akin to a shop owner thinking he can drum up business by dressing down his customers for not buying more products. At that point, you're arguing with your customers, and you oughtn't be surprised when look they askance at you.
Lecturing Internet users on cookies and advertisements amounts to a solution in search of a problem. What cookies and ads do they want users to accept? Cookies for which they don't see a real benefit? Ads that obnoxiously prevent them from productively using their browsers? Users who see a benefit to accepting cookies and not blocking ads will accept cookies and view
advertisements without being pressured to do so; those who don't won't. And it simply won't do to try shame them into doing otherwise.
One Last Excuse...
Hired mouthpieces for Corporate America have been offering one last excuse for scuttling privacy legislation: the
availability of applications (such as the ones listed on this web site) that consumers can use to protect their
privacy. Lest anyone assume that I, the author of a web site with links to many privacy & security programs, think that such programs offer sound reasons for quashing governmental privacy protections, let me assure you that such an assumption would be false.
I can offer several reasons for rejecting the idea that privacy software
provides a good excuse not to establish privacy protections through legislation:
- Despite the laudable efforts of privacy & security software designers to make their applications usable, this software remains much too complex and technical for the vast majority of home users. Privacy ought not be only for those with the time and technological savvy to figure out how to setup and use this software.
- The means and methods used by corporations to violate the privacy of citizens and consumers online are often well beyond the understanding of typical users of the Internet. Privacy ought not be afforded only to those with the technical background and investigative determination to keep up.
- The capabilities of the technologies employed by corporations to monitor and track consumer behavior are escalating at a ferocious pace, and privacy software will inevitably lag in providing protection against these new technologies. Privacy ought not be only for those who live on the "bleeding edge" of technological change.
- While a good deal of quality privacy software is available for free, many programs are expensive. Privacy ought not be only for those who can afford to pay for it.
- Corporate America is increasingly resorting to intellectual property law (e.g.,
UCITA, the DMCA, and the CBDTPA) to limit, if not cut off, the legal options that consumers and citizens have when they go online or use software. Privacy ought not be only for those with the required bankroll, political muscle, and high-powered attorneys to force legislation through Congress or a legal case through the court system.
- The infrastructure of the Internet is slowly becoming consolidated in the hands of a few large conglomerations of corporate interests, allowing those powerful interests to set the terms and conditions for access to the Internet. Privacy ought not be only for those with the hard cash or good fortune to acquire a reliable, independent connection to the online world outside of such sterile corporate playgrounds.
So, please do use this web site to check out and acquire the software and information that you need in order to protect your privacy and security on the Internet. But don't be deceived into thinking that any of the applications you find here represent permanent privacy solutions.
More importantly, though, be conscious of the fact that while you may have had the good fortune to enjoy the time, attention, technological savvy, and (perhaps) money to install and use these software applications, the majority of your friends, family, neighbors, co-workers, relatives, and fellow citizens have not.
Still With Me?
If you are interested in doing more reading about your privacy in an online world, I can offer you several places to start:
- Have a look at this list of Privacy Groups, Coalitions, and Portals. There are many fine, worthy organizations that are working hard to protect your privacy on the Internet, and they have a wealth of information and advice to offer you.
- You can also check out this list of Introductory Privacy Guides & Overviews. Lots of good reading here, especially if you're new to this topic.
- For more nitty-gritty information about protecting your privacy online, have a look through the links on the Privacy
Documents & FAQ's page as well as the General Privacy Information page.
- If you'd like to chat about privacy and security issues in Usenet style newsgroups with others, or if you have questions about Internet privacy and security (esp. software and hardware questions), check out the several GRC Discussion Groups, which are generously hosted by Steve Gibson of Gibson Research Corp, or the DSLReports Security forum. There are a variety of groups to choose from at GRC, and many friendly, knowledgeable folks who hang out in both the DSLR and GRC forums.
- Finally, if you are especially industrious, you might read one of the more important and influential essays on privacy ever written: "The Right to Privacy" by Samuel Warren and Louis Brandeis. Though published over 100 years ago, it remains a burningly relevant, surprisingly prescient, and thought-provoking meditation on the nature and importance of personal privacy. PDF and Word doc versions available here.)
|