| First Things First: What Version Do You Have? | |
| Before we get started, let's figure out what version of Internet Explorer you're running. You'll need to know this information for some of the steps we go through later. | |
| To find your version of Internet Explorer, click Help >> About Internet Explorer on the Internet Explorer menu bar... | |
 |
|
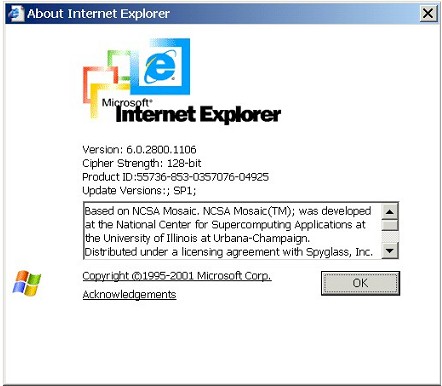
| A small box should open up with version information. | |
 |
|
|
|
| Click the OK button to close this box when you have the information you need. | |
| AOL Web Browser | |
| The AOL web browser is actually just a fancy front-end to Internet Explorer. Although you may not have realized it, when you're surfing the web with AOL's web browser, you're actually using Internet Explorer underneath. Moreover, the AOL web browser relies upon the same privacy and security settings that we'll discuss in this document. | |
| Different versions of AOL install different versions of Internet Explorer. To find out what version of Internet Explorer is installed on your system, you'll have to locate and open Internet Explorer itself, instead of just the AOL web browser. Look on your desktop or your Start menu for an icon that resembles the following: | |
| Once you find such an icon, double-click on it to open Internet Explorer. With Internet Explorer open, you can locate the version information that we describe above. | |
| You can also locate version information for Internet Explorer from within the AOL web browser itself. Use the AOL Keyword BROWSER. You'll receive a small box with version information for Internet Explorer: | |
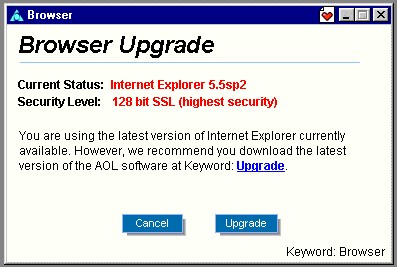 |
|
| The Current Status: line lists the version of Internet Explorer that the AOL web browser is using (Internet Explorer 5.5 with SP2, in this case). | |
| By the way, if you're an AOL subscriber, you're not restricted to using the AOL web browser for your web surfing. After you've established a connection to AOL, you can minimize the AOL program and open Internet Explorer as we did just above and surf the Internet as you normally would. To access AOL's special areas and content (including your AOL email account), you'll have to use the AOL program that you normally do. | |
| In the next section, we'll describe how to access the privacy and security settings from within the AOL browser. | |
| Clearing Junk from the General Tab | |
| First, we'll clear some routine
junk that accumulates every time you surf the Web with Internet
Explorer.
Many users find it helpful to clear this junk every time they finish surfing the web. It only takes a few seconds, and it helps keep your browser and PC free of junk that can degrade system performance and compromise your privacy. For more information on the privacy issues involved with this junk -- which accumulates in the URL History and Temporary Internet Files -- see THIS page. |
|
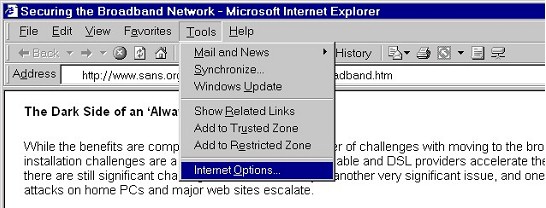
| 1. | Open the Internet Options Box |
| All of Internet Explorer's privacy and security settings can be accessed from the Internet Options box. To open Internet Options, select Tools >> Internet Options... on the menu bar. (If you're using any version of Internet Explorer 4, select View >> Internet Options...) | |
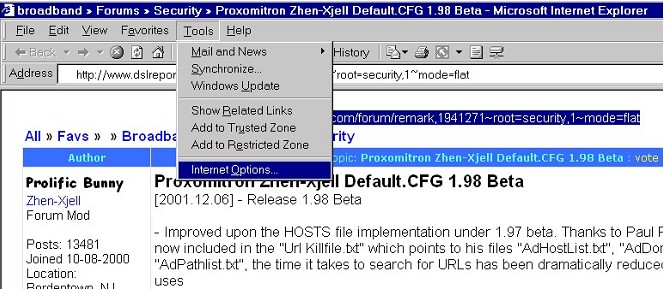
|
|
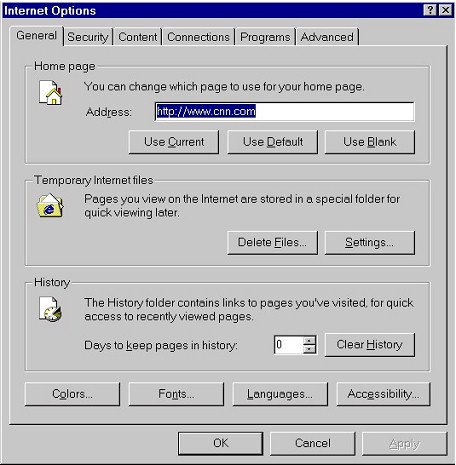
| The Internet Options box will open. (If you're not an AOL user, you can move ahead to the next step.) | |
| AOL Internet Properties | |
| The AOL web browser is actually just a fancy
front-end to Internet Explorer. Although you may not have realized it,
when you're surfing the web with AOL's web browser, the AOL browser is actually
using Internet Explorer underneath. AOL's embedded Internet Explorer web
browser does rely upon the privacy and security settings from Internet
Explorer. Not only can you clear the browser cache (Temporary Internet
Files) and URL History, but AOL's web browser will respect the Internet
zone Security settings that we'll discuss in the next
section. From within the AOL web browser you can access the same Internet Options box that you find in standard versions of Internet Explorer. In AOL, go to Settings >> Preferences. |
|
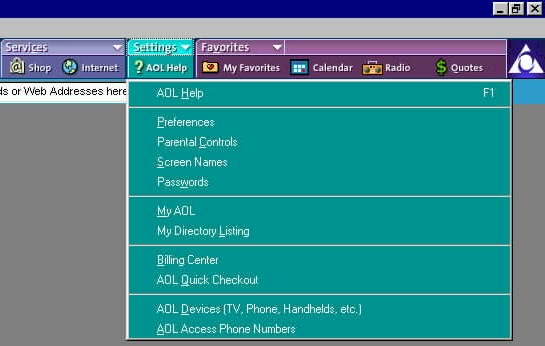 |
|
| On the Preferences box that pops up, you'll see a link to Internet Properties (WWW). Click on that link. | |
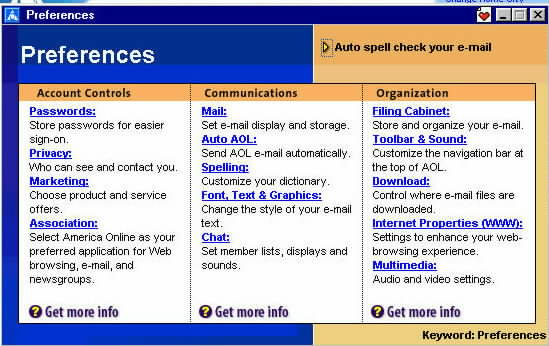 |
|
| A dialog box titled AOL Internet Properties will open. | |
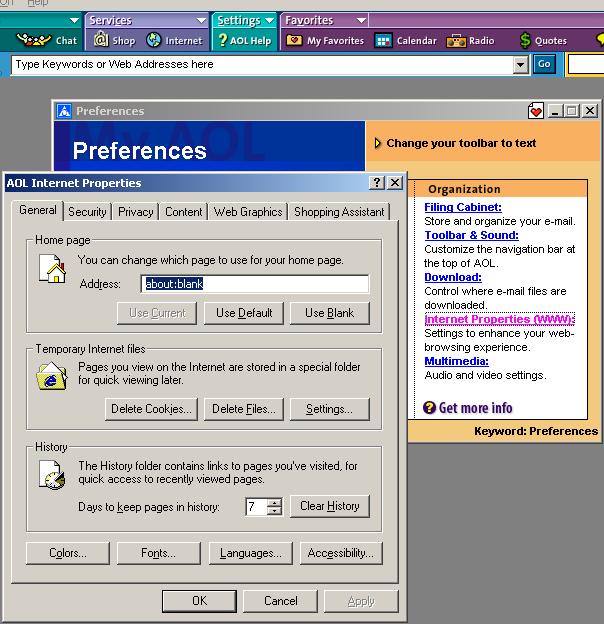 |
|
| This is essentially the same Internet Options box that we discuss in the rest of this document. From this box you can access all the privacy and security settings that we'll cover in this document, with the possible exception of the Internet Explorer 6.0 Privacy settings, depending on what version of Internet Explorer is installed on your system. To find out what version of Internet Explorer your AOL web browser is relying upon, see the first section of this document. | |
| 2. | Delete Temporary Internet Files & History |
| The Internet Options box opens on the General tab. On this tab we can delete Temporary Internet files as well as the URL History (which automatically clears the typed URL dropdown list as well). | |
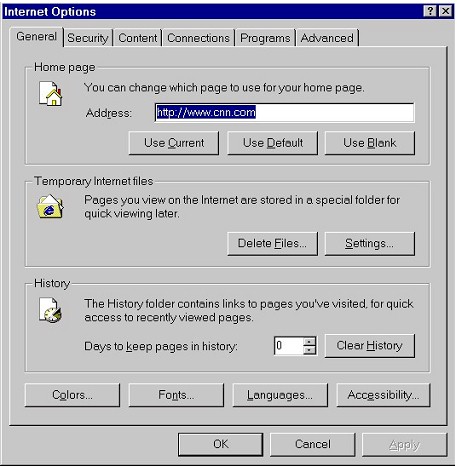 |
|
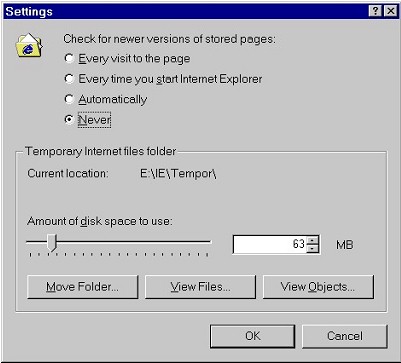
| Note that we can also set this History to be kept in number of days. Many users set this number to 0, as in the screenshot above, to prevent the History being saved across browsing sessions. | |
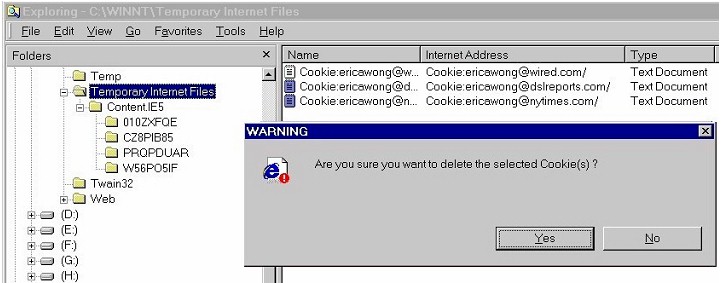
| 3. | Delete Cookies (Internet Explorer 6.0 only) |
| If you're running Internet Explorer 6.0, you will see one additional button that is not present in earlier versions of Internet Explorer: a Delete Cookies... button. This button will clear all cookies from Internet Explorer 6.0. | |
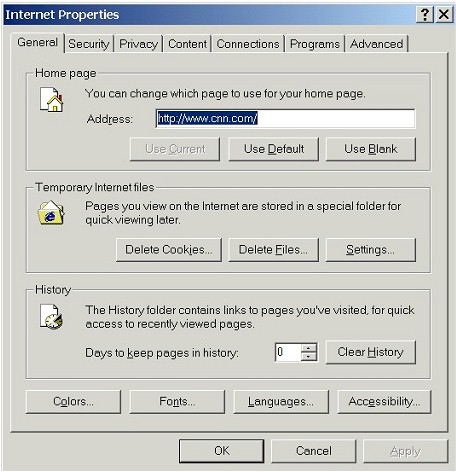 |
|
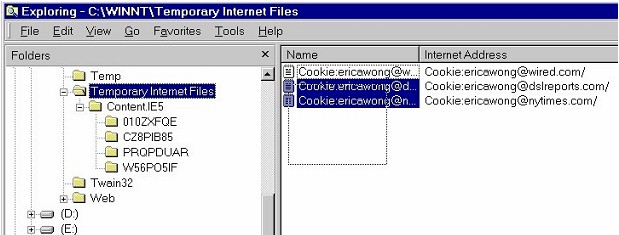
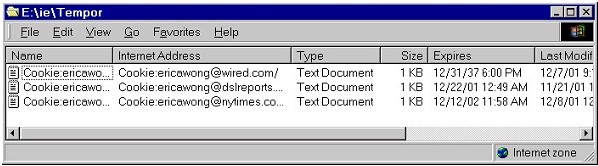
| Remember: this Delete Cookies button appears only in Internet Explorer 6.0, not previous versions of Internet Explorer. If you're running an earlier version of Internet Explorer and want to delete cookies, then you'll have to delete cookies from the Temporary Internet Files directory (see the fifth section on this page below for instructions). | |
| Delete All Cookies? | |
| Keep in mind that if you delete all cookies, some web
sites, esp. those with which you have registered, may not work properly
or may fail to recognize you when you return. You might want to keep
cookies for those kinds of web sites.
If you do want to keep any cookies, then you'll have to use some other strategy to manage cookies. Instead of using this Delete Cookies button, you can:
|
|
| Securing the Internet Zone | |
|
Next, we'll switch to the Security tab so that we can securely configure such things
as ActiveX, Java, and Scripting. We'll also configure
Cookies, but only in pre-IE 6.0
versions of Internet Explorer (Internet Explorer 6.0 uses
the Privacy tab to configure
cookies, which we'll discuss later
on this page).
AOL Web Browser Remember: if you're using the AOL web browser, your web browser relies on Internet Explorer and will respect the Security settings we describe below. To learn how to access these settings within AOL's web browser, see the previous section. Once you securely configure the Security settings as we describe below, you may need to take one additional step to ensure that all of AOL's services and web sites remain functional on your computer. See the note on AOL Services & Web Sites below for more information. Finally, the AOL web browser does allow you to configure other preferences related to your privacy and security, however, these preferences are specific to AOL itself (i.e., they're not part of the Internet Explorer browser that AOL relies upon). You can get a brief overview of these other AOL preferences on THIS page. |
|
| 1. | Switch to the Security Tab |
| Click on the Security tab so that we can access Internet Explorer's security zones. | |
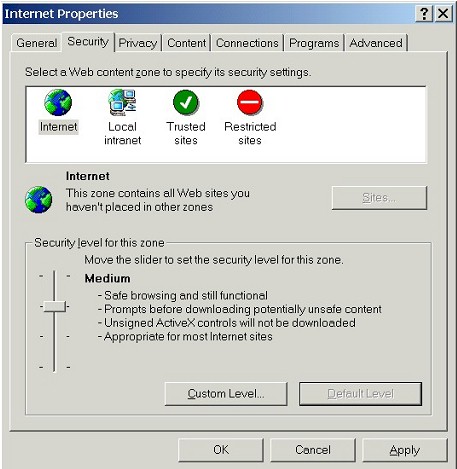
|
|
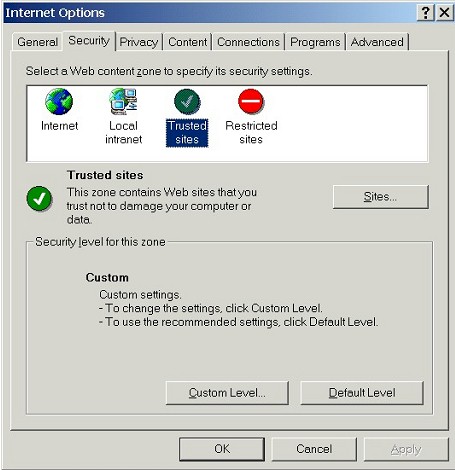
| The Security tab allows us to select the zone we wish to configure and then configure it. | |
| Working with Security Zones | |
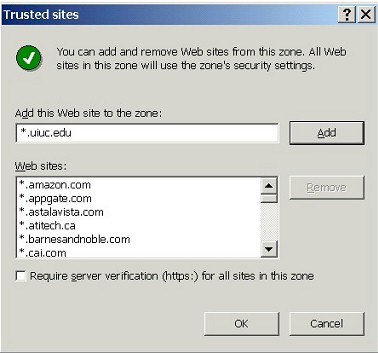
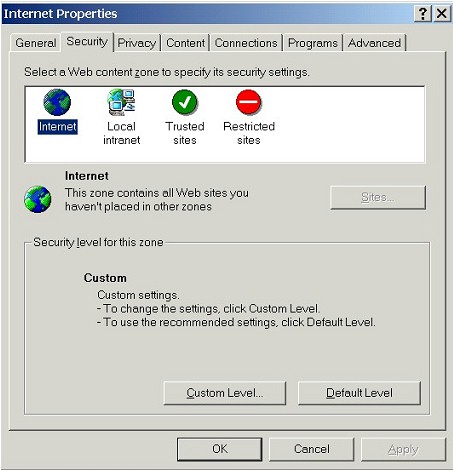
| Internet Explorer classifies web sites by Security zone: Internet, Local intranet, Trusted sites, Restricted sites. Each zone has its own set of security settings, allowing users to force web sites to follow different security policies, depending on the level of trust for those web sites. By default, all web sites fall into the Internet zone unless they're added by the user to one of the other zones. When we visit a web site for the first time, for example, it will fall within the Internet zone. If we don't add it to another zone (e.g., the Trusted sites or Restricted sites zone), it will remain in the Internet zone. | |
| As most users won't ever bother to add sites to other zones, we'll just configure the Internet zone. A secure Internet zone has significant benefits. A securely configured Internet zone gives us a high level of protection, because all web sites fall by default within that zone, esp. unfamiliar sites we may be visiting for the first time. Thus, we'll never be unpleasantly surprised by a web site that we're visiting for the first time. Web sites that we know and trust and which may require looser security settings can be added to the Trusted sites zone (see below for advice on using the Trusted sites zone). | |
| Once we select the zone we wish to configure, we can either adjust the Security level slider (to High, Medium, Medium-low, or Low), or we can select Custom Level... and configure all the privacy and security settings for each zone one-by-one. (Each of the four settings on the slider uses a pre-set combination of all the individual settings that we can custom configure ourselves.) Once we custom configure a zone, the slider for that zone will disappear: | |
 |
|
| Active Content & the Security Zones | |
To securely configure the Internet zone, we will
focus on three main groups of settings:
These "active content" technologies can be used by web sites to add useful functionality to otherwise drab, static web pages. They can also be used to install spyware and adware on your PC, hijack your web browser, and compromise your privacy and security. For more information on the privacy and security issues involved with "active content," see THIS page. In what follows we will disable these forms of "active content" in the Internet zone to prevent them from being used by malicious web sites to compromise your privacy and security. |
|
| Warning: Broken Web Sites | |
| Once we disable "active content" in the Internet zone, some web sites that rely on those technologies may not work properly. To allow web sites that you know and trust to function, you can those sites to the Trusted sites zone, which follows a more lenient set of security polices. See the instructions below for help on adding sites to the Trusted sites zone. | |
| 2. | Bring Up the Custom Level for the Internet Zone |
| Click on the Internet zone icon to select it, and then hit the Custom Level... button. | |
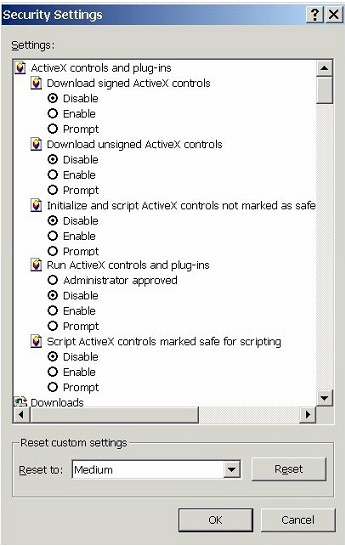
| 3. | Configure ActiveX controls and plug-ins |
| At the top of the Security Settings box that pops up are all of our settings for ActiveX controls and plug-ins. | |
 |
|
| (Note that I've doctored this screenshot just a bit so that we can see all of the settings at once. You'll probably have to scroll down to get to some of the lower settings.) | |
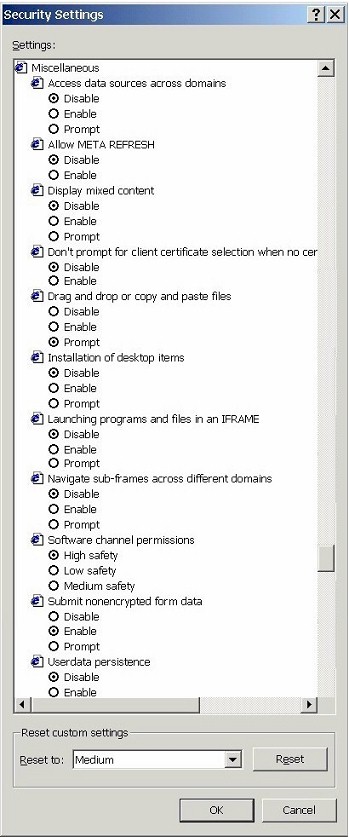
| Change all settings for ActiveX controls and plug-ins to Disable. (Prompt might initially seem like a good compromise between Enable and Disable, but most users will be unable to cope with the flood of popup confirmation boxes that result.) | |
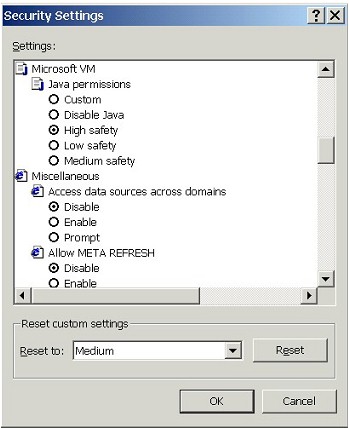
| 4. | Configure Microsoft VM (Java permissions) |
| If we scroll down a bit, we encounter the
settings for Java permissions (under Microsoft VM -- VM
stands for Virtual Machine, in case you were wondering).
Here we can select a safety level for Java. |
|
 |
|
| The most secure setting is, obviously, High safety. | |
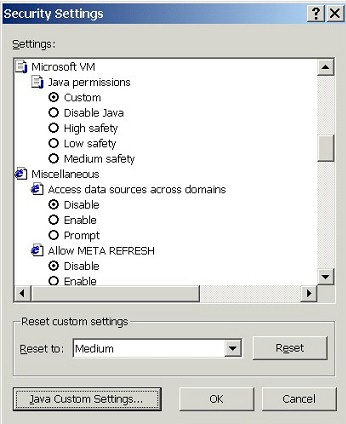
| There's another method to configure Java permissions, though. Instead of choosing a preconfigured safety level, we can also select the Custom option... | |
 |
|
| ...and then hit the Java Custom Settings... button to bring up a detailed list of Java settings that we can custom configure. | |
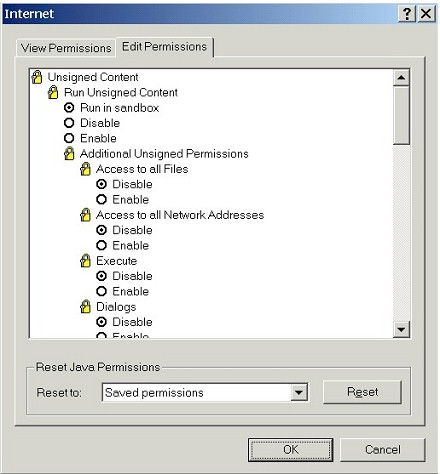 |
|
| Most home users will find it simpler to select a pre-configured safety level, as we did above, though. Unless you know what these settings are, they are not worth bothering with. | |
| 5. | Configure Scripting |
| Scrolling down still further, we encounter our Scripting settings. | |
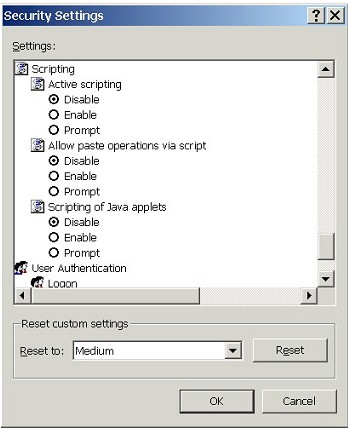 |
|
| Change all Scripting settings to Disable. | |
| Warning: Broken Web Sites | |
| Remember: once we disable such things as Scripting or ActiveX controls and plug-ins, or set Java permissions to High safety, some web sites may not work properly. In such cases we can add those sites (assuming we trust them) to our Trusted sites zone. Once those sites are added to the Trusted sites zone (which uses a different set of security settings), they should start working again. See the last section on this page for details on how to use the Trusted sites zone. | |
| Where to Go Next... | |
| If you're using Internet Explorer 6.0, then your job in the Internet Options box is through. Move to the next section in order to configure Cookies on the Privacy tab. | |
| If you're using an earlier version of Internet Explorer, then you're not quite through, because you can also configure Cookies within the Security Settings box. (Internet Explorer 6.0 users configure cookies on the Privacy tab -- see the next section for instructions.) | |
| AOL Services & Web Sites | |
| Securely configuring the Internet zone (as we've done
above) may cause problems for some of AOL's services and web
sites. If you lock down the Internet zone using the settings
described above and you find that certain aspects of AOL don't work
anymore, there's a simple solution: add the aol.com domain to
your Trusted sites zone.
Once aol.com added to your Trusted sites zone (which uses a different set of security settings than the Internet zone we've configured here), AOL's services and web sites should start working again. See the last section on this page for details on how to add items like aol.com to the Trusted sites zone. |
|
| 6. | Configure Cookies |
| Cookies are small "data tags" that allow web
sites to recognize us when we return to those web sites. While cookies
can be useful -- say, for being recognized at a web site with which
we've registered -- they can also be used by advertisers to track our
movements and behavior across the Net. To protect our privacy, we need
to configure Internet Explorer's cookie settings so that the
browser stores only cookies that we find useful. For more information on
the privacy issues involved with cookies, see THIS
page.
While Internet Explorer 4, Internet Explorer 5, and Internet Explorer 6 are very similar in most of their privacy and security settings, they present different options for handling cookies.
|
|
| In this step, we'll discuss cookie configuration for Internet Explorer 5 and Internet Explorer 4. If you're using Internet Explorer 6, you can skip this step and move directly to the last step in this section. | |
| Internet Explorer 5.0x & 5.5x | |
| For any version of Internet Explorer
5,
you can configure Cookies within the Security Settings for each zone.
(Note: the screenshot you see below is from Internet Explorer 5. ) |
|
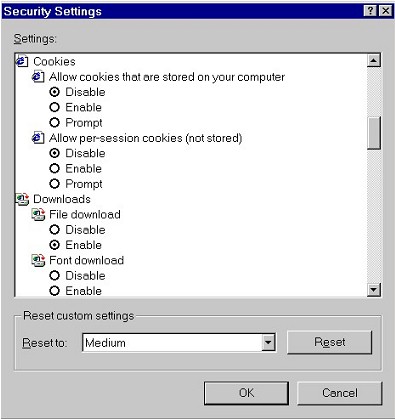 |
|
| Note that "cookies stored on your computer" are permanent cookies that are saved to your hard drive for future use by web sites. By contrast, "per-session cookies" are temporary cookies that are automatically deleted once you close Internet Explorer. These are usually not a problem. (Session cookies are frequently used for the virtual "shopping carts" employed by merchandising sites like Amazon.com and CDNow.) | |
| If you wish to preserve some cookies for certain web sites, then you should not disable "stored" cookies. You will need to selectively manage and delete cookies -- see the section entitled Selectively Deleting & Managing Cookies for details. | |
| Internet Explorer 4.0x | |
| Internet Explorer 4 does not allow you to configure
cookies by Security zone. If you're using Internet Explorer 4, you'll have to close the Internet
zone Security Settings box (click Apply, then OK) and switch to the Advanced tab.
There you'll find a similar looking group of cookie settings under the Security
section.
(Note: the screenshot you see below is from Internet Explorer 4. You won't find any cookie settings on the Advanced tab in Internet Explorer 5 or 6.) |
|
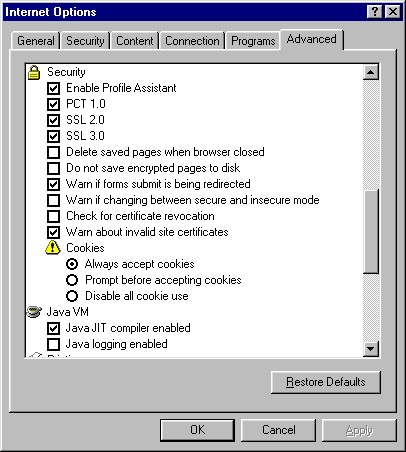 |
|
| The cookie settings you see on the Advanced tab apply to all the security zones -- there's no way to configure cookies for each zone separately, unlike Internet Explorer 5.0x and 5.5. Moreover, the options we have are fairly limited (Enable, Prompt, Disable) -- there's no way to distinguish between permanent cookies and session cookies (as we can do with Internet Explorer 5) or first-party vs. third-party cookies (as we can do with Internet Explorer 6). | |
| If you wish to preserve some cookies for certain web sites, then you should not disable cookies. You will need to selectively manage and delete cookies -- see the section entitled Selectively Deleting & Managing Cookies for details. (You could select Prompt, but most users will quickly tire of barrage of prompts when surfing the web.) | |
| Note: Other Versions of Internet Explorer
For Internet Explorer 6, you'll need to use the Privacy tab to set cookies, as the settings we discussed above aren't available in Internet Explorer 6 (see the next section for instructions). |
|
| 7. | Close Security Settings / Internet Options Boxes |
| If you're using Internet Explorer 4 or 5, click Apply and OK to close the Security Settings box, then OK again to close Internet Options. At this point you should learn how to Selectively Delete & Manage Cookies. You may also want to read about how to Add Sites to the Trusted Zone. | |
| If you're using Internet Explorer 6, move on to the next section to learn how to configure cookies on the Privacy tab. | |
| Managing Cookies On the Internet Explorer 6.0 Privacy Tab | |
| Cookies are small "data tags" that allow web
sites to recognize us when we return to those web sites. While cookies
can be useful -- say, for being recognized at a web site with which
we've registered -- they can also be used by advertisers to track our
movements and behavior across the Net. To protect our privacy, we need
to configure Internet Explorer's cookie settings so that the
browser stores only cookies that we find useful. For more information on
the privacy issues involved with cookies, see THIS
page.
Internet Explorer 6 does not allow us to configure cookies from the Security tab or the Advanced tab, as we just did for Internet Explorer 4 and 5 above. With Internet Explorer 6, we configure cookies on the Privacy tab, which is right next to the Security tab. (If you don't see a Privacy tab on the Internet Options box, then you haven't got Internet Explorer 6, and you can safely skip this section.) |
|
| The Privacy Tab, Cookies, & Security Zones | |
| The cookies settings on the Privacy tab apply to the Internet zone only. Cookies are blocked by default in the Restricted sites zone and accepted by default in the Trusted sites zone. There is no easy way to change cookie settings for those two zones, unlike Internet Explorer 4 and Internet Explorer 5. Internet Explorer 6, however, gives us many more options for controlling cookies in the Internet zone. | |
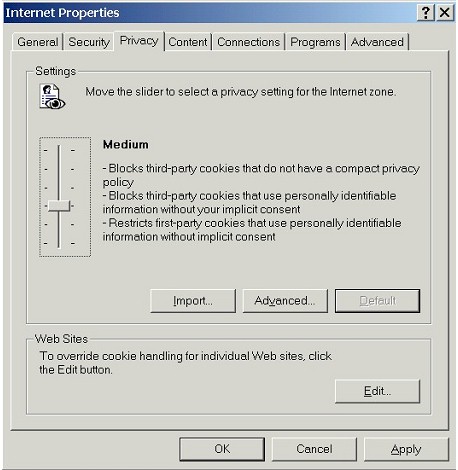
| 1. | Switch to the Privacy Tab |
| To configure cookies for Internet Explorer 6.0, switch to the Privacy tab. | |
 |
|
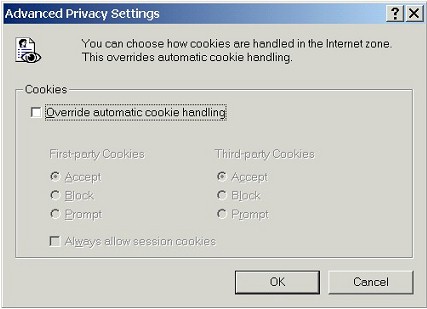
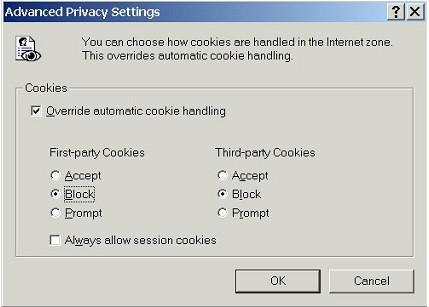
| It's important to recognize that we have a range of choices to make here. The Privacy tab allows us to configure cookies in three different ways. We can: | |
|
|
| Keep in mind that these three different methods for configuring and controlling cookies are mutually exclusive: we can only use one method at a time. We can't mix and match methods. Once we use one method to configure cookies, any changes we've made using the other methods are ignored or disabled. | |
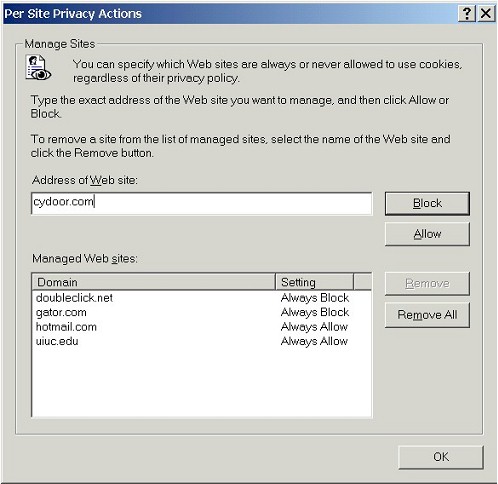
| Whatever method we choose to configure cookies, we can also add specific web sites to the Web Sites - Per Site Privacy Actions list, so that cookies from those individual sites will always be blocked or allowed, no matter what our other settings are (except when the Settings slider bar is set to Block All Cookies or Accept All Cookies). | |
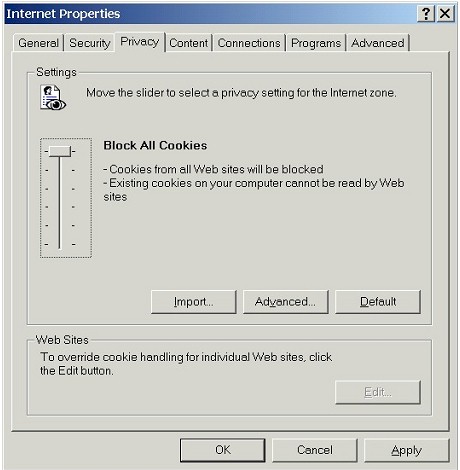
| 2. | Adjust the Settings Slider |
| Most home users will initially find it easiest to adjust the Settings slider bar,
primarily because it is presented front-and-center on the Privacy
tab and because the slider appears to be a simple way to "ratchet
up" one's privacy. We'll cover the Settings slider bar
first, but I'm going to suggest that the Settings slider bar is deceptively
simple and doesn't give you nearly as much privacy protection as
some of the other options that are available for cookies in Internet
Explorer 6.0.
You can move the Settings slider bar up and down. Pay attention to the descriptions of each slider setting as you move the slider bar up and down from level to level. |
|
 |
|
| Block All Cookies is, obviously, the most restrictive setting, and it will do just what the name suggests. | |
| There are other settings to choose from on the slider bar, though. Here's a summary of all six settings with accompanying descriptions: | |