|
The Anatomy of a "Drive-by-Download" by Eric L. Howes Contents
Introduction
[return to top] Note: some hyperlinks in this HTML version of
"The Anatomy of a 'Drive-by-Download'" have been disabled to
prevent |
||||||||||||||||||||||||||||||||||||||||||||||||||
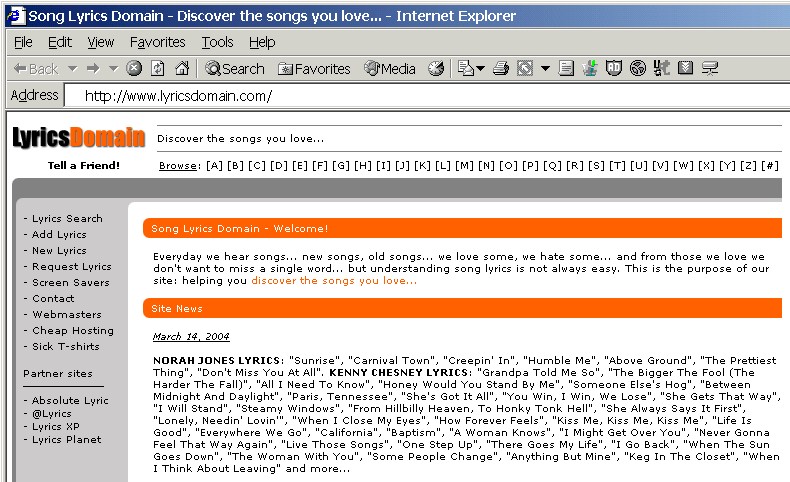
| The Installation [return to top] On March 23, 24, and 26, I visited a web site named LyricsDomain (http://www.lyricsdomain.com/). This web site purports to help users with the lyrics to popular songs:
In fact, it is a web site that distributes advertising software from C2 Media, known to many web surfers as Lop.com after one of the company's main web sites ("lop" stands for "live online portal"). There is nothing on the home page of the LyricsDomain site, however, that overtly indicates its association with C2 Media.
Figure 1: LyricsDomain home page The site's privacy policy (http://www.lyricsdomain.com/privacy.html) is fairly innocuous and even appears to be "consumer friendly":
Although I was familiar with lyricsdomain.com and the software that I would encounter there, many consumers would not be, and that lack of familiarity with the web site or C2 Media could very well play a crucial role in determining how average consumers handle the "drive-by-download" process at LyricsDomain. The "Security Warning" Box
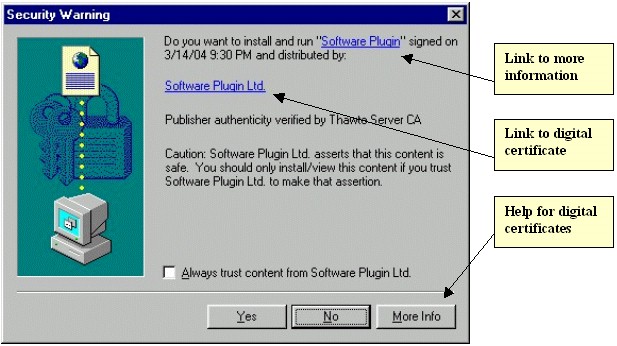
Figure 2: "Security Warning" for "Software Plugin" This is the standard warning box that Internet Explorer provides users for ActiveX controls loaded by web sites. Unless they have changed the security settings for the Internet zone in Internet Explorer, users should see this warning box whenever they encounter a page that attempts to install an ActiveX control on their systems. This particular warning box resulted from a hidden IFRAME (a window within a window) in the HTML of the LyricsDomain home page. That IFRAME loaded another small page (count.htm) that itself used JavaScript to begin the installation of a 12 kb ActiveX control named download.mp3.exe from lyricsdomain.com. As we shall see, this small ActiveX control was a stub downloader that would be used to download and install several megabytes of other software -- in total, eight different programs from at least three different vendors. That whole installation process, though, started with the automated installation of this small, innocuously named file described simply as "Software Plugin."
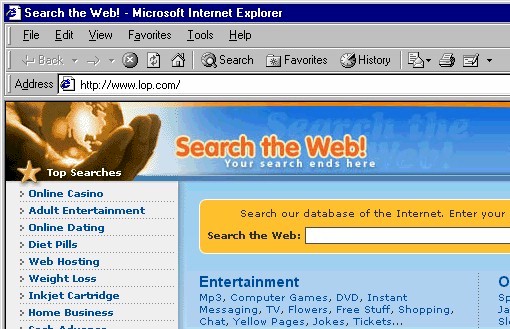
Figure 3: "Search the Web!" home page Not only does this home page have no clearly discernible connection with the named software vendor ("Software Plugin Ltd."), but it contains no information at all about the software being installed. There is no EULA (end user license agreement) or any other information that might help the user understand the company or the nature of its software. Even at this stage there is no indication that C2 Media is involved in this process at all (though savvy internet users might recognize the domain name lop.com). There is a small "Help" link at the bottom of the page (not shown in Figure 3 above) that does take users to a page with information about C2 Media's or Lop.com's software
(http://www.lop.com/help.html). It is doubtful that most users would even know enough to click that "Help" link, and those did could be forgiven for not understanding the relationship of the software described on that page with the "Software Plugin" being installed by LyricsDomain.
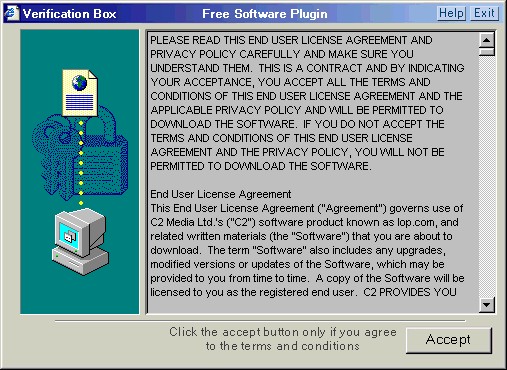
At this point we have seen nothing to indicate anything untoward or suspicious about the "Software Plugin." In fact we have gotten very little information at all. The License Agreement That situation changed dramatically once I clicked the "Yes" button in the "Security Warning" box (see Figure 2 above) and agreed to proceed with the installation. Another dialog box popped up with a license agreement (see Figure 6 below).
Figure 6: "Verification Box - Free Software Plugin" This license agreement is no simple matter. In fact, this license agreement for "Free Software Plugin" contains not one license agreement, but EULAs and privacy policies for three different companies. By clicking the "Accept" button in this "Verification Box," users are in fact consenting to the
installation of a whole raft of software, not just the "Free Software Plugin."
Table 1: Summary of License Agreements and Privacy Policies It took me almost an hour to plow through these licenses and privacy policies in a careful manner and extract the key terms of the agreements, though even now I have to wonder if I caught everything significant and understood it properly. I think it entirely uncontroversial to state that this kind of document (or set of documents) could be read wholly and productively only by a practicing attorney -- and even then only one with endless amounts of time and patience.
The Download & Install
Table 2: Installed Programs Some explanation of this breakdown of installed programs is in order. I have identified and classified the programs that were installed not only by examining the directories and files that were created on my hard drive, but by reviewing the license agreements and looking for key words. The uninstallation information contained in the Add/Remove Programs Control Panel applet proved useful as well, especially for determining the names of some applications. I have also based this classification on the scan results from
SpyBot Search & Destroy and
Ad-aware, two anti-spyware programs that I used to clean up my system (see the last section, "The Cleanup," for more details). In some cases I have consulted online resources in order to identify the programs for what they were. As a general rule I have regarded software as a clearly distinguishable program when it was installed in a unique directory (e.g., C:\Program Files\SysAI vs. C:\Program Files\AutoUpdate). Although each of those directories might have contained several executable files, I have still classified those files as a single program or application. Concluding Remarks
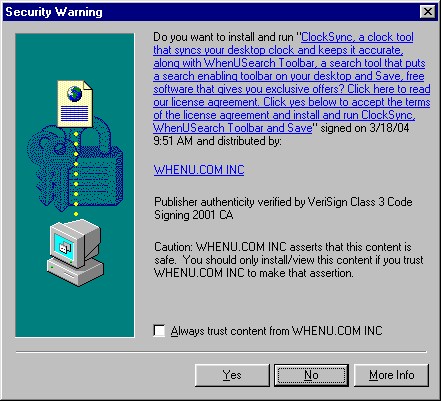
Figure 7: "Security Warning" for "ClockSync" Some vendors even link to the program's EULA from the "Security Warning" box, as indeed WhenU.com does with this warning box for ClockSync. |
||||||||||||||||||||||||||||||||||||||||||||||||||
| The Aftermath [return to top] The eight programs installed on my PC made numerous changes and additions to the system, some more visible and noticeable than others. In this short section I summarize the most obvious or visible changes and additions that resulted. It should be noted that this software was installed and running on my system for less than half an hour. Consequently, there may be other effects of these programs that would become apparent only weeks or months after installation and which I cannot describe or account for here. Also, I did not perform any packet sniffing or other network forensics, so I cannot describe or account for network connections established by these software programs or the data packets they transmitted to other entities on the internet. Toolbars The first and most obvious change to my system was the addition of not one, but three different toolbars by C2 Media's Window Active, Window Searching, and ErrorOnce programs.
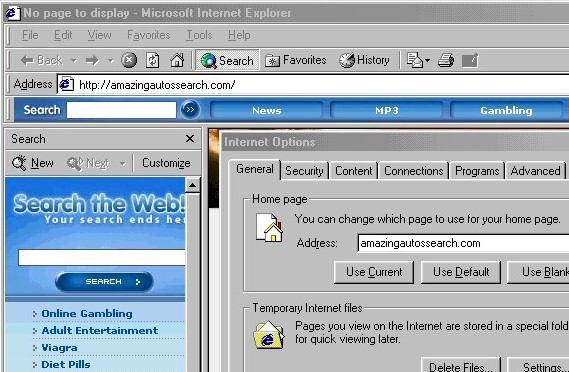
Toolbar # 1 was the first to appear, and it popped up right on the desktop. A floating toolbar, it was constantly in the way, even after I closed my browser. Toolbar # 2 appeared within Internet Explorer right under the address bar. I could right-click on it and deselect it from the list of visible Internet Explorer bars to make it disappear, but it would reappear the next time I opened Internet Explorer. Toolbar # 3 appeared towards the bottom of my desktop, as if attached to the taskbar. It appeared only when Internet Explorer was open, though. C2 Media assigns these toolbars different names (Accessory Toolbar, Desktop Toolbar, Pass-Through Toolbar), though which is which I cannot say. Moreover, why it is necessary to have three toolbars, all with apparently overlapping functionality, is a mystery. I did not use any of these toolbars so I cannot report on their actual functionality or other characteristics. Suffice it to say, they were a major annoyance simply because of the screen space they wasted. Browser & Desktop Modifications C2 Media's programs made other modifications to my browser, however. Most significantly, its software reset my default home page from cnn.com to amazingautossearch.com, another site associated with C2 Media. It also reset the default search engine preferences to amazingautossearch.com so that every search I did directly through the browser itself (as opposed to visiting a search site like Google) would be sent through C2 Media. Figure 11 shows Internet Explorer with the Internet Options box open (note the default home page) and the search bar opened on the left to the amazingautossearch.com search page.
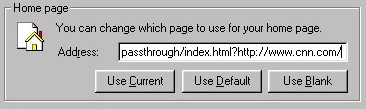
Figure 11: Hijacked Home Page and Search Bar After I attempted to restore my home page to cnn.com, C2 Media's software reset my home page yet again to re-route access to it through amazingautossearch.com/passthrough, which acted as a kind of re-direct or proxy. Figure 12 shows my default home page after I attempted to change it:
Figure 12: Passthrough Home Page Hijack I did not attempt to restore any of my search preferences.
Finally, C2 Media's software dropped a number of new icons or internet shortcuts on my desktop for online sites and services. Somewhat less annoying than the three toolbars, the new Favorites and desktop icons were, nonetheless, useless clutter. Dialog Box Advertisements One other annoying addition to my system was an advert bar at the bottom of common Windows dialog boxes, presumably so that were I ever in the middle of saving a file or printing a document and found myself suddenly overcome with the spontaneous urge to buy something or enter a sweepstakes contest, I could do so quickly and effortlessly.
Figure 15: Alset HelpExpress Dialog Ad This particular system modification was the handiwork of the Alset HelpExpress program. As with the toolbars from C2 Media, I did not use this feature and thus cannot comment on its functionality. Pop-ups, Pop-ups, Pop-ups All three software vendors warned in their license agreements that their applications would serve pop-ups and other forms of advertising (see Table 1 above), and indeed there was no shortage of pop-ups for me to close. With programs from three vendors running in the background and serving up pop-up advertising, it was almost impossible to tell which program was responsible for any given pop-up, though their frequency seemed to increase as I visited more and more web pages. At one point in my brief experience with this collection of software, I was closing pop-ups every five to ten seconds, and sometimes multiple pop-ups at a go. Web surfing speed also declined, presumably because there were so many programs exchanging data with external network entities (uploading information, downloading advertisements) and consuming bandwidth. I even experienced random browser crashes, undoubtedly because of the sheer number of pop-ups, toolbars, and programs clambering for attention on my system. Other Programs / Summary Several programs installed on my PC had no immediate, visible effects on the system. In particular, the AutoUpdate program from AdIntelligence and the mysterious Rads01.Quadrogram were "silent," yet both were configured to execute on Windows startup and could be found running in the task list. The AutoUpdate program likely updates the AdIntelligence software, though I never saw it do so. Just what Rads01.Quadrogram was doing is not clear; its functionality may have become apparent had I kept it installed for longer than I did, however. |
||||||||||||||||||||||||||||||||||||||||||||||||||
| The Cleanup [return to top] As we saw earlier ("The Installation") the process of installing this collection of advertising programs was fairly simple, provided we didn't ask too many questions or demand readable, straightforward descriptions of the software. The process of removing this software, by contrast, was quite difficult and time-consuming. Although there were vendor-supplied uninstallers for most of the programs, they were not always easy to find. Moreover, most of them didn't work completely. To remove this advertising software completely, I had to use three different anti-spyware programs (SpyBot Search & Destroy, Ad-aware, HijackThis!). At the end of the entire process I still had some minor cleanup work to do by hand. The complete uninstallation process that I used can be divided into four stages:
Readers should bear in mind that I went into this uninstallation process well-prepared. Not only did I know what to look for, but I had taken careful notes during the installation process. I had read the license agreements and noted key URLs and company names. Thus, I knew the programs that had been installed and the web sites to visit to find vendor-supplied uninstallers. Moreover, I had good anti-spyware tools at hand and was experienced in using them. I also had recourse to anti-spyware web sites to get key information about files, directories, and Registry keys. Finally, I am an experienced user of Windows PCs. Thus, I am familiar with the directory structure on Windows PCs as well as the process for editing the Windows Registry. 1. Run vendor-supplied uninstallers already on the system Vendors of advertising software tout the uninstallers they provide for their programs. In fact, some vendors even include clauses in their EULAs prohibiting consumers from using third-party tools (read: anti-spyware applications) to remove or uninstall their programs. So I decided to start with the vendor-supplied uninstallers that I could find on my PC. Not all of the programs had left uninstallers on my PC during the installation process, however, so the next step was to track down other uninstallers on vendor web sites and run.
Table 3: Vendor-Supplied Uninstallers The Add/Remove Programs Control Panel applet contained entries for only four programs that had been installed by these vendors: Window Active, Window Searching, HelpExpress, and Coupons and Offers. Of course, to use those uninstallers, one must recognize the entries for what they are. I happened to be very familiar with what was already installed on my PC, so this was not a problem. Other less experienced users might have difficulty identifying the Add/Remove Program entries to remove, especially given the generic names used by some of these programs and the fact that several of the programs' names were never clearly announced during the installation process. 2. Obtain and run vendor-supplied uninstallers from web sites I found uninstallers for the C2 Media products on the amazingautossearch.com "Help" page
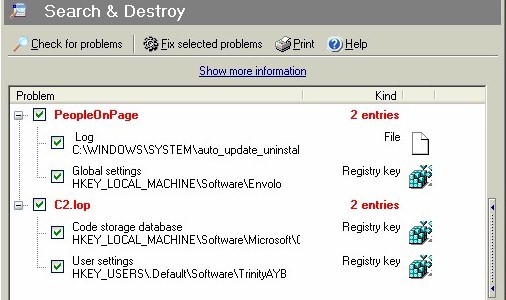
(http://amazingautossearch.com/help.html). That page offered two uninstallers -- toolbar_uninstall.exe and new_uninstall.exe -- so I grabbed them both. Neither of these uninstallers completely removed the remnants of C2 Media's programs, though they came close: the Window Active directory was completely removed. A few stray Registry keys remained, however, as did the original stub installer download.mp3.exe (in C:\Windows\Downloaded Program Files). 3. Run anti-spyware programs I first ran SpyBot Search & Destroy 1.3 beta 6, a well-regarded and free anti-spyware utility from PepiMK. With the latest available definitions (4 Mar. 2004), SpyBot Search & Destroy flagged several problems on my PC (see Figure 16 below), all of which were related to the software installed in this example "drive-by-download."
Figure 16: SpyBot Search & Destroy scan results The "C2.lop" and "PeopleOnPage" entries are files or Registry entries left behind on my system by the vendor-supplied uninstallers. (PeopleOnPage is in fact AdIntelligence.) While none of these entries represented serious problems, they had to go. I let SpyBot fix every problem it identified.
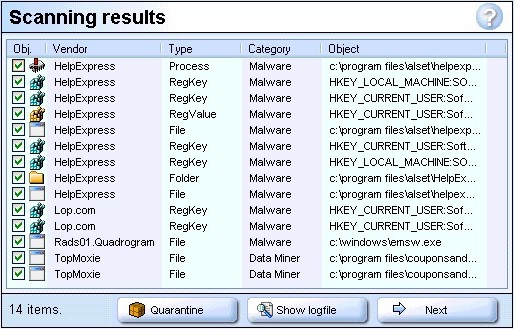
Figure 17: Ad-aware "Scanning results" Ad-aware found the files and Registry keys for Alset HelpExpress, which had been left substantially intact by the Alset uninstallers I had run earlier. It also found some leftover files from Coupons and Offers (named TopMoxie by Ad-aware) and a few remaining Registry keys for C2 Media's programs. Both Coupons and Offers and the C2 Media programs had already been effectively disabled, however -- what Ad-aware found was just more leftover garbage. Finally, Ad-aware found the Rads01.Quadrogram executable (emsw.exe), which strangely enough was still in the Windows directory. One of the vendor-supplied uninstallers had obviously killed the process for Rads01.Quadrogram and removed the auto-run entry from the Registry (none of the anti-spyware programs found that Registry entry); the executable file had survived, however. As with SpyBot, I let Ad-aware fix every problem it identified.
The "R1" entry is a search bar hijack left over from C2 Media's software (note that it points Internet Explorer's search bar to amazingautossearch.com). The "O2" entry is for a broken BHO (browser helper object, a kind of plug-in for Internet Explorer) -- the Registry entry is still there for C2 Media's ErrorOnce BHO, however, the file necessary to run that BHO is missing (undoubtedly removed by one of the uninstallers or anti-spyware programs run previously). I used HJT to fix both of these problems. 4. Perform manual cleanup By this point I was completely familiar with the files that had been installed during this "drive-by-download" test, so it wasn't hard to find stray detritus that survived the vendor-supplied uninstallers as well as the anti-spyware programs. There were still some files left over in installation directories for Coupons and Offers and Alset (HelpExpress). An uninstaller for AutoUpdate has been left in C:\Windows\System. Although none of what remained represented a serious problem, it all should have been cleaned up much earlier. |
||||||||||||||||||||||||||||||||||||||||||||||||||
| Conclusion [return to top] From start to finish this automated "drive-by-download" installation experience was an unpleasant undertaking. Although it began with the fairly innocuous prompt to install the "Software Plugin," it became progressively more difficult and frustrating. The installation process initially provided almost no helpful information about the software to be installed. Key program functionality was then obscured behind an impenetrable wall of legalese, which few consumers would have any hope of understanding. And though a careful review of the license agreements and privacy policies revealed that most of the functionality of the software installed on my PC had in fact been disclosed, the effects of that software on my system were serious inasmuch as the new toolbars and endless advertising interfered with the normal use of the computer. Finally, the job of cleaning up and removing the software proved to be a long and cumbersome process, even for someone who had the experience and tools to do it. Consumers who encounter the "Software Plugin" at the LyricsDomain web site and mistake it for a simple browser plug-in necessary to use the music content of the site are in for a nasty surprise. After clicking but two buttons -- "Yes" in the "Security Warning" box and "Accept" in the "Verification Box" -- they will be treated to the installation of eight different programs from at least three different vendors. Three new toolbars will be added to their systems. Their browser's home page and search preferences will be hijacked, and they will be inundated with pop-up advertising. So thoroughly does this advertising software penetrate the system, users will be confronted with advertising even when they print documents or save files. To clean this mess up on my own PC, I had to run four different uninstallers from Add/Remove Programs or program installation directories, only to find that I had to download and run three more uninstallers from vendor web sites. Even then my system was not clean. Three different anti-spyware tools were required to remove most of what was left, including one advertising program that the vendor's uninstallers had simply failed to uninstall. At the end there were still a few stray files and directories left for me to remove by hand. Compared with what could have happened, however, I got off easy. My internet connection was not broken, and I have no reason to fear the arrival of the next phone bill. My system remained fairly stable, though I did experience a few browser crashes, and system performance took an enormous hit. Moreover, though the removal process proved to be a time consuming chore, I was ultimately able to install and run anti-spyware programs. Despite being somewhat difficult to remove, the advertising software did not deliberately undermine my removal efforts or sabotage my system, as other unwanted spyware is known to do. Nonetheless, this example "drive-by-download" should illustrate the enormous difficulties that consumers face when they encounter apparently innocuous software that is presented to them in misleading and confusing contexts. Not surprisingly, they are complaining, and we would do well to understand the reasons for those complaints and take action to solve the problem. 29 March 2004 |
||||||||||||||||||||||||||||||||||||||||||||||||||
| More Information [return to top] For more information on the software discussed in this document, see the following sources: Anti-Spyware Programs
Advertising Software Programs
Related Documents [return to top]
© 2004 Eric L. Howes |