| Index
PGP Installation Note: Click on
thumbnail pictures to view full-size screenshots. |
||
| PGP Installation | ||
| Shot | Caption | Comments |
 |
Welcome | This is the first screen you see after running SETUP.EXE. |
 |
License Agreement | You have to agree to the terms of the EULA before you can continue. |
 |
What's New | This is a summary of new & noteworthy features in this version of PGP. |
 |
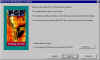
User Information | Here you should enter Name & Company info. |
 |
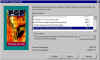
Choose Destination Location | Tell the setup program where you want PGP installed. You can customize the location by clicking the Browse button. |
 |
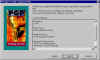
Select Components | Select the components that you want to install. If you're not doing any work with VPN's (virutal private networks), then I'd recommend unchecking the PGPnet Virtual Private Networking box. Don't forget to check the appropriate plugins for your email client, though plugins aren't necessary to use PGP with email clients. |
 |
Ready to start copying Files | The setup program reviews what it will do to install PGP on your system. |
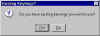 |
Existing Keyrings? | If you've used PGP before, you can direct the setup program to install keyrings you previously created and used. If you're a new user to PGP, click No. |
 |
Setup Complete | Setup is complete; you should reboot before continuing so that all the changes to your system can take effect. |
| PGP On the Desktop | ||
| Shot | Caption | Comments |
 |
PGP on the Start menu | You can launch PGP programs from your Start menu. |
 |
PGPtray icon next to the clock | PGPtray runs in the background and can be accessed from the padlock icon next to the clock. |
 |
PGPtray icon w/ context menu popped up |
Click on the PGPtray icon to get a menu of options. These contain many of the same functions that you find in the Start menu program group seen above. |
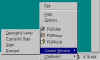 |
Current Window menu of the PGPtray icon |
This is the core of PGP. The Current Window menu options allow you to encrypt, decrypt, sign, and verify whatever text happens to be in the window with focus. Although you can use plugins with some email clients, you can perform the same functions with this Current Window menu. |
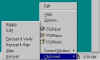 |
Clipboard menu of the PGPtray icon |
This Clipboard menu is similar to the Current Window menu. You can copy text to the Windows clipboard (Edit >> Copy, from w/in any application) and then perform functions on it from here. You'll have to Paste the result back into the appropriate document or email. |
 |
PGPtools toolbar | You can access many PGP functions using this toolbar. Move your mouse over the buttons to get labels for each of the buttons. You can launch this toolbar either from the Start menu or the PGPtray icon. |
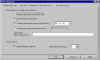 |
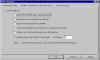
PGP Options (1) | One tab from the PGP Options configuration box. Look carefully through these options. If you need more help in understanding any of the options, consult the Help files that come with PGP. You can access this PGP Options configuration box either from the Start menu or the PGPtray icon. |
 |
PGP Options (2) | Another tab from the PGP Options configuration box. |
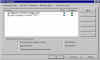 |
PGP Options (3) | Still another tab from the PGP Options configuration box. |
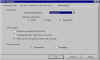 |
PGP Options (4) | One final tab from the PGP Options configuration box. There are a few other tabs that we haven't seen here, but these four are the most important. |
| PGP Key Pair Generation | ||
| Shot | Caption | Comments |
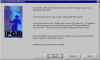 |
Key Generation Wizard | This is at the heart of PGP -- generating a key pair for yourself and setting up a keyring. The Key Generation Wizard walks you through the steps of generating a key pair for yourself. The Key Generation Wizard will launch the first time you select PGPkeys either from the Start menu or the PGPtray icon. |
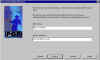 |
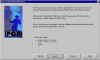
specify Full name and Email address |
Your key pair will be associated with a particular name and email address. |
 |
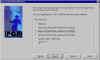
choose Key Pair Type | Either one of these key pair types is fine (though hard core crypto gurus might prefer one over the other). |
 |
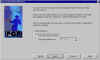
choose Key Pair Size | If you've got an older, slower computer, you might choose a smaller key pair size. If you've got a new, fast computer, go for one of the larger sizes. The larger the key size, the stronger it is (though key size isn't the only factor here). |
 |
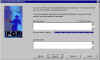
set Key Pair Expiration | Some folks prefer to expire their key pairs on pre-defined dates and then generate new ones. They do so for security reasons. When your key pair expires, however, you'll also have to revoke your public key from any key servers to which you have posted your public key. |
 |
Passphrase generation | This process is critical. A weak passphrase means weak protection for your private key. PGP cannot protect your private key if you choose a weak passphrase simply because you find it easy to remember.If you need tips for generating a strong passphrase that you can still remember easily, see one of the many helpful online documents that discuss passphrases. |
 |
generating Key Pair | PGP generates a key pair for you based on the selections you just made above. |
 |
send Public Key to server | You can post your public key (one half of your key pair) to a special key server on the internet where others can access it in order to send encrypted email to you. There are other ways to share your public key with people, however -- see the PGP Help documentation for more info. We discuss ways to publish your public key in the next section. |
 |
Congratulations! | Hey, you've completed one of the most important parts of setting up and configuring PGP for use ! |
 |
PGPkeys (the Keyring) | Your keyring stores your own key pair as well as the public keys that you've collected from other people in order to send encrypted email to those people. |
 |
backup Keyring prompt | You should backup your keyring. |
 |
Public Keyring Backup | Backing up your keyring involves saving two files -- one for your public keys... |
 |
Private Keyring Backup | ...and one for your private key. |
| PGP Public Key Posting | ||
| Shot | Caption | Comments |
 |
PGP Keyserver | In order to let other people email us with encrypted messages, we have to give them our public key.
Once they have our public key, they can use it to encrypt messages to us (and
we can encrypt messages to them using their public keys). One of the easier ways to make our public key available to other people is by posting our public key on a keyserver. People can retrieve our public key from that keyserver and then use it to email us. Two commonly used keyservers are at http://pgpkeys.mit.edu/ and http://wwwkeys.us.pgp.net/, though these aren't the only ones. |
 |
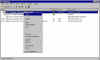
adding key to keyserver through web site (1) |
We can add or post our public key to the keyserver through a web form interface at either one of the keyservers. |
 |
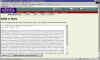
copying public key in order to paste it into web form |
First we have to copy our public key from our keyring in PGPkeys... |
 |
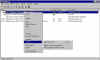
adding public key to keyserver through web site (2) |
And then we paste it into the web form and submit it. |
 |
sending public key to server through PGPkeys |
We can also send our public key to the keyserver through PGPkeys. |
 |
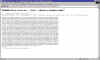
searching for a key on the keyserver web site (1) |
If we want to email someone who uses PGP and encrypted message, we first need to retrieve our recipient's public key. We can search through a web form at one of the keyservers. We can search on name or email address. |
 |
searching for a key on the keyserver web site (2) | And here are the results of our search. We can save this block of text as a plain text file and then import it into our keyring. |
 |
importing someone's public key into our keyring |
Importing someone's public key into our keyring from a plain text file (.txt) or ASCII Armor file (.asc) is easy. |
 |
searching for a key on keyserver through PGPkeys |
We can also search for public keys on the keyservers and then import them directly through PGPkeys. Once we have someone's public key on our keyring, we can use it to email encrypted messages to that person. |
 |
sending public key through email | One other means for us to give someone our public key (or obtain someone else's public key) is through email. Again, here we've simply copied our public key from PGPkeys and then pasted it into an email. If we receive someone else's public key through email, we can save that email as a plain text file (.txt) and then import it through PGPkeys. |